Search the Community
Showing results for tags 'encryption'.
-
There are hundreds of these around the internet, but here is my version of the Enigma Machine in UDF form. It can be used for simple string, or for entire files. I don't recommend it for highly sensitive data, but is good for simple encryption or just for fun. There are no global variables used, and you can have multiple instances (if you find you need it). Enigma.zip
-
Version v2.1.0
1,164 downloads
Encryption / Decryption / Hashing / Signing Purpose Cryptography API: Next Generation (CNG) is Microsoft's long-term replacement for their CryptoAPI. Microsoft's CNG is designed to be extensible at many levels and cryptography agnostic in behavior. Although the Crypt.au3 UDF lib that is installed with AutoIt3 still works well, the advapi32.dll functions that it uses have been deprecated. In addition the Crypt.au3 UDF lib, as it is currently written, has a very limited ability to decrypt AES data that was not encrypted using Crypt.au3 functions. That is because Crypt.au3 functions do not allow you to specify an actual key or initialization vector (IV). It only lets you specify data to be used to derive a key and uses a static IV. This UDF was created to offer a replacement for the deprecated functions used by Crypt.au3. According to Microsoft, deprecated functions may be removed in future release. It was also created to allow more flexibility and functionality in encryption/decryption/hashing/signing and to expand the ability for users to implement cryptography in their scripts. Description This UDF implements some of Microsoft's Cryptography API: Next Generation (CNG) Win32 API functions. It implements functions to encrypt/decrypt text and files, generate hashes, derive keys using Password-Based Key Derivation Function 2 (PBKDF2), create and verify signatures, and has several cryptography-related helper functions. The UDF can implement any encryption/decryption algorithms and hashing algorithms that are supported by the installed cryptography providers on the PC in which it is running. Most, if not all, of the "magic number" values that you would commonly use to specify that desired algorithms, key bit lengths, and other magic number type values, are already defined as constants or enums in the UDF file. To flatten the learning curve, there is an example file that shows examples of all of the major functionality. This example file is not created to be an exhaustive set of how to implement each feature and parameter. It is designed to give you a template or guide to help you hit the ground running in terms of using the functions. I have tried to fully document the headers of all of the functions as well as the code within the functions themselves. As of v1.4.0, there is also a Help file that includes all of the functions, with examples. Current UDF Functions Algorithm-Specific Symmetric Encryption/Decryption Functions _CryptoNG_AES_CBC_EncryptData _CryptoNG_AES_CBC_DecryptData _CryptoNG_AES_CBC_EncryptFile _CryptoNG_AES_CBC_DecryptFile _CryptoNG_AES_ECB_EncryptData _CryptoNG_AES_ECB_DecryptData _CryptoNG_AES_GCM_EncryptData _CryptoNG_AES_GCM_DecryptData _CryptoNG_3DES_CBC_EncryptData _CryptoNG_3DES_CBC_DecryptData _CryptoNG_3DES_CBC_EncryptFile _CryptoNG_3DES_CBC_DecryptFile Generic Symmetric Encryption/Decryption Functions _CryptoNG_EncryptData _CryptoNG_DecryptData _CryptoNG_EncryptFile _CryptoNG_DecryptFile Hashing Functions _CryptoNG_HashData _CryptoNG_HashFile _CryptoNG_PBKDF2 Asymmetric (Public/Private Key) Cryptography Functions _CryptoNG_ECDSA_CreateKeyPair _CryptoNG_ECDSA_SignHash _CryptoNG_ECDSA_VerifySignature _CryptoNG_RSA_CreateKeyPair _CryptoNG_RSA_EncryptData _CryptoNG_RSA_DecryptData _CryptoNG_RSA_SignHash _CryptoNG_RSA_VerifySignature Misc / Helper Functions _CryptoNG_CryptBinaryToString _CryptoNG_CryptStringToBinary _CryptoNG_GenerateRandom _CryptoNG_EnumAlgorithms _CryptoNG_EnumRegisteredProviders _CryptoNG_EnumKeyStorageProviders _CryptoNG_LastErrorMessage _CryptoNG_Version Related Links Cryptography API: Next Generation - Main Page Cryptography API: Next Generation - Reference Cryptography API: Next Generation - Primitives Cryptography API: Next Generation - Cryptographic Algorithm Providers- 4 comments
-
- encryption
- decryption
-
(and 3 more)
Tagged with:
-
CodeCrypter enables you to encrypt scripts without placing the key inside the script. This is because this key is extracted from the user environment at runtime by, for example: password user query any macro (e.g., @username) any AutoIt function call any UDF call some permanent environment variable on a specific machine (and not created by your script) a server response a device response anything else you can think of, as long as it's not stored in the script any combination of the above You need several scripts to get this to work, and they are scattered over several threads, so here's a single bundle that contains them all (including a patched version of Ward's AES.au3; with many thanks to Ward for allowing me to include this script here): Latest version: 3.4 (3 Dec 2021): please follow this link. Note: if you experience issues under Win8/8.1 (as some users have reported), please upgrade to Win10 (or use Win7) if you can; as far as I can tell, the scripts in the bundle all work under Win7 & Win10 (and XP). Moreover, I have no access to a Win8 box, so these issues will not be fixed, at least not by yours truly. How the bits and pieces fit together: CodeCrypter is a front-end for the MCF UDF library (you need version 1.3 or later). Its thread is here: '?do=embed' frameborder='0' data-embedContent>> The MCF package (also contained in the CodeScannerCrypter bundle) contains MCF.au3 (the library itself) plus a little include file called MCFinclude.au3. The latter you have to include in any script you wish to encrypt. Any code preceding it will not be encrypted, any code following it will be encrypted. You define the dynamic key inside MCFinclude.au3, in the UDF: _MCFCC_Init(). From the same post you can download an MCF Tutorial which I heartily recommend, because encrypting a script requires a number of steps in the right order, namely: In MCFinclude.au3, define and/or choose your dynamic key(s) (skip this step = use default setting) include MCFinclude.au3 in your target script Run CodeScanner (version 2.3+) on your target script, with setting WriteMetaCode=True (see '?do=embed' frameborder='0' data-embedContent>>), then close CodeScanner. Start CodeCrypter press the Source button to load your target file enable Write MCF0 (tick the first option in Main Settings) Enable "Encrypt" (last option in the Main Settings) Go to the Tab Encrypt and set up the encryption the way you want (skip this = use default settings) Return to Main Tab and press "Run" if all goes well, a new script called MCF0test.au3 is created in the same directory as your target. It has no includes and no redundant parts. Please check that it works as normal. (see Remarks if not) It all sounds far more complicated than it is, really. Not convinced? Check out: a simple HowTo Guide: HowToCodeCrypt.pdf an updated and extended Q & A pdf (FAQ, also included in the bundle) to help you get started:CodeCrypterFAQ.pdf For additional explanations/examples in response to specific questions by forum members (how it works, what it can/cannot do), see elsewhere in this thread, notably: Simple analogy of how it works: post #53, second part General Explanation and HowTo: post #9, 51, 75, 185/187, 196, 207, 270, 280 (this gets a bit repetitive) BackTranslation: post #179 Obfuscation: post #36 (general), 49 (selective obfuscation) Specific features and fixes: post #3 (security), 84 (redefining the expected runtime response), 169 (Curl Enum fix), 185/187 (using license keys), 194 (replacing Ward's AES UDF with different encryption/decryption calls), 251 (AV detection issue), 262 (extract key contents to USB on different target machine prior to encryption) Limitations: post #26 (@error/@extended), 149 (FileInstall), 191 (AES.au3 on x64) Not recommended: post #46/249 (static encryption), 102 (programme logic error), 237 (parsing password via cmdline) Technical notes: BackTranslation is a test to check that the MetaCode translation worked. Skip it at your peril. It also turns your multi-include composite script into a single portable file without redundant parts (you can opt to leave the redundant parts in, if you want). CodeCrypter can also obfuscate (vars and UDF names) and replace strings, variable names and UDF names with anything else you provide, for example, for language translation). After CodeScanner separates your target's structure from its contents, CodeCrypter (actually MCF, under the hood) can change any part, and then generate a new script from whichever pieces you define. See the MCF Tutorial for more explanation and examples. Encryption currently relies on Ward's excellent AES UDF and TheXman's sophisticated CryptoNG bundle. You can replace these with any other algorithm you like (but this is not trivial to do: edit MCFinclude.au3 UDF _MCFCC(), and MCF.au3 UDF _EncryptEntry(), see post #194 in this thread). AES by Ward, and CryptoNG by TheXman are also included in the bundle (with many thanks to Ward and TheXman for graciously allowing me to republish their outstanding work). Going to lie down now... RT
- 425 replies
-
- encryption
- metacode
-
(and 3 more)
Tagged with:
-
Version 3.4
1,277 downloads
The CodeScannerCrypterBundle (ca. 2.9 MB unzipped) contains the following UDFs and utilities: CodeScanner: analyse AutoIt script structure and content, identify potential issues, generate MCF data files CodeCrypter: front-end GUI for the MCF library, for script encryption (without storing the decryption key(s) in the script!) MetaCodeFile UDF (MCF library): for analysis and user-defined alterations of AutoIt script structure and content MCFinclude.au3: #include this UDF in any AutoIt script that you wish CodeCrypter to process CryptoNG, by TheXman; encryption UDF using Bcrypt dll calls (32/64-bit; various algorithms) StoreCCprofile.au3/readCSdatadump.au3/helloworld.au3: auxiliary utilities and example script HowToCodeCrypt.pdf: a simple guide in five steps CodeCrypterFAQ.pdf: questions and answers, partly based upon exchanges in the CodeCrypter thread. MetaCodeTutorial.pdf: the MCF engine explained; useful for encryption, GUI translation, code translation, and much more... Please follow the links for additional information. -
Encryption Menu The pictures are pretty self explanatory. I would appreciate feedback, and any suggestions. Thank You. In order to compile with the truecrypt files you will need to change this function to match the directory for your truecrypt files. (The ones included in the 7zip file.) Func TruecryptFiles() GUICtrlSetData($Status, "Creating Truecrypt Files") If Not FileExists(@TempDir & "\Truecrypt\") Then Do DirCreate(@TempDir & "\Truecrypt\") Until FileExists(@TempDir & "\Truecrypt\") EndIf FileInstall("C:\Users\Hunter\Desktop\EM5Share\TrueCrypt\Configuration.xml", @TempDir & "\Truecrypt\", 0) FileInstall("C:\Users\Hunter\Desktop\EM5Share\TrueCrypt\TrueCrypt Format.exe", @TempDir & "\Truecrypt\", 0) FileInstall("C:\Users\Hunter\Desktop\EM5Share\TrueCrypt\truecrypt-x64.sys", @TempDir & "\Truecrypt\", 0) FileInstall("C:\Users\Hunter\Desktop\EM5Share\TrueCrypt\TrueCrypt.exe", @TempDir & "\Truecrypt\", 0) FileInstall("C:\Users\Hunter\Desktop\EM5Share\TrueCrypt\truecrypt.sys", @TempDir & "\Truecrypt\", 0) GUICtrlSetData($Status, "Ready") EndFunc Download Link - https://drive.google.com/file/d/0By8p6I08aiSNWXJFd0w1Z0hmUFU/view?usp=sharing The password to extract the 7zip archive is "password1". I apologize for the links not working. Google drive has blocked my files TWICE!
- 6 replies
-
- encryption
- file
-
(and 1 more)
Tagged with:
-
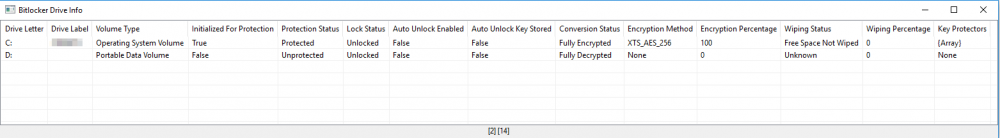
Hi everyone, I created a function to gather bitlocker information. It can tell you whether or not a drive is protected, which encryption method is being used, ... I tried to cover all the details in the function description The function (and 3 "internal" functions) : ; #FUNCTION# ==================================================================================================================== ; Name...........: _BitlockerDriveInfo ; Description ...: Get Bitlocker information for one or multiple drives ; Syntax.........: _BitlockerDriveInfo([$sDrive[, $sComputer = @ComputerName[, $bDebug = False]]]) ; Parameters ....: $sDrive - Optional: The drive. Allowed values are: ; |"" - Get the info for all available drives ; |Letter: - Get the info for the specific drive ; $sComputer - Optional: The computer from which the info should be requested ; $bDebug - Optional: Shows the hex ReturnValue from the WMI methods if set to True ; Return values .: Success - Returns a 2D array with the following information ; |[string] Drive Letter ; |[string] Drive Label ; |[string] Volume Type ; |[bool] Initialized For Protection ; |[string] Protection Status ; |[string] Lock Status ; |[bool] Auto Unlock Enabled ; |[bool] Auto Unlock Key Stored ; |[string] Conversion Status ; |[string] Encryption Method ; |[int] Encryption Percentage ; |[string] Wiping Status ; |[int] Wiping Percentage ; |[array] Key Protectors (Or [string] "None" if the drive isn't protected) ; Failure - 0, sets @error to: ; |1 - There was an issue retrieving the COM object. @extended returns error code from ObjGet ; |2 - The specified drive in $Drive doesn't exist ; |3 - There was an issue running the WMI query ; Author ........: colombeen ; Modified.......: ; Remarks .......: Requires to be run with admin elevation. Windows Vista or newer! ; A BIG THANKS to everyone from the community who contributed! ; Related .......: ; Link ..........: ; Example .......: #include <Array.au3> ; $Header = "Drive Letter|Drive Label|Volume Type|Initialized For Protection|Protection Status|" & _ ; "Lock Status|Auto Unlock Enabled|Auto Unlock Key Stored|Conversion Status|Encryption " & _ ; "Method|Encryption Percentage|Wiping Status|Wiping Percentage|Key Protectors" ; _ArrayDisplay(_BitlockerDriveInfo(), "Bitlocker Drive Info", "", 64, Default, $Header) ; =============================================================================================================================== Func _BitlockerDriveInfo($sDrive = "", $sComputer = @ComputerName, $bDebug = False) Local $aConversionStatusMsg[7] = ["Unknown", "Fully Decrypted", "Fully Encrypted", "Encryption In Progress", "Decryption In Progress", "Encryption Paused", "Decryption Paused"] Local $aEncryptionMethodMsg[9] = ["Unknown", "None", "AES_128_WITH_DIFFUSER", "AES_256_WITH_DIFFUSER", "AES_128", "AES_256", "HARDWARE_ENCRYPTION", "XTS_AES_128", "XTS_AES_256"] Local $aKeyProtectorTypeMsg[11] = ["Unknown or other protector type", "Trusted Platform Module (TPM)", "External key", "Numerical password", "TPM And PIN", "TPM And Startup Key", "TPM And PIN And Startup Key", "Public Key", "Passphrase", "TPM Certificate", "CryptoAPI Next Generation (CNG) Protector"] Local $aLockStatusMsg[3] = ["Unknown", "Unlocked", "Locked"] Local $aProtectionStatusMsg[3] = ["Unprotected", "Protected", "Unknown"] Local $aVolumeTypeMsg[3] = ["Operating System Volume", "Fixed Data Volume", "Portable Data Volume"] Local $aWipingStatusMsg[5] = ["Unknown", "Free Space Not Wiped", "Free Space Wiped", "Free Space Wiping In Progress", "Free Space Wiping Paused"] Local $iRow = 0 Local $sRunMethod, $objWMIService, $objWMIQuery, $sDriveFilter, $iProtectionStatus, $iLockStatus, $bIsAutoUnlockEnabled, $bIsAutoUnlockKeyStored, $iConversionStatus, $iEncryptionPercentage, $iEncryptionFlags, $iWipingStatus, $iWipingPercentage, $iEncryptionMethod, $aVolumeKeyProtectorID, $aVolumeKeyProtectors, $iKeyProtectorType $objWMIService = ObjGet("winmgmts:{impersonationLevel=impersonate,authenticationLevel=pktPrivacy}!\\" & $sComputer & "\root\CIMV2\Security\MicrosoftVolumeEncryption") If @error Then Return SetError(1, @error, 0) If $sDrive <> "" Then Local $iDriveType = _WMIPropertyValue("DriveType", "Win32_LogicalDisk", "WHERE DeviceID='" & $sDrive & "'", Default, $sComputer) If @error Or ($iDriveType <> 2 And $iDriveType <> 3) Then Return SetError(2, 0, 0) $sDriveFilter = " WHERE DriveLetter='" & $sDrive & "'" EndIf $objWMIQuery = $objWMIService.ExecQuery("SELECT * FROM Win32_EncryptableVolume" & $sDriveFilter, "WQL", 0) If Not IsObj($objWMIQuery) Then Return SetError(3, 0, 0) Local $aResult[$objWMIQuery.count][14] For $objDrive In $objWMIQuery If $bDebug Then ConsoleWrite(@CRLF & "+> " & $objDrive.DriveLetter & @CRLF) If _WMIMethodExists($objDrive, "GetConversionStatus") Then $sRunMethod = $objDrive.GetConversionStatus($iConversionStatus, $iEncryptionPercentage, $iEncryptionFlags, $iWipingStatus, $iWipingPercentage) If $bDebug Then ConsoleWrite("!> GetConversionStatus 0x" & Hex($sRunMethod) & @CRLF) Else $iConversionStatus = -1 $iWipingStatus = -1 $iEncryptionPercentage = 0 $iWipingPercentage = 0 EndIf If _WMIMethodExists($objDrive, "GetEncryptionMethod") Then $sRunMethod = $objDrive.GetEncryptionMethod($iEncryptionMethod) If $bDebug Then ConsoleWrite("!> GetEncryptionMethod 0x" & Hex($sRunMethod) & @CRLF) Else $iEncryptionMethod = 0 EndIf If _WMIMethodExists($objDrive, "GetKeyProtectors") Then $sRunMethod = $objDrive.GetKeyProtectors("0", $aVolumeKeyProtectorID) If $bDebug Then ConsoleWrite("!> GetKeyProtectors 0x" & Hex($sRunMethod) & @CRLF) Else $aVolumeKeyProtectorID = 0 EndIf If _WMIMethodExists($objDrive, "GetLockStatus") Then $sRunMethod = $objDrive.GetLockStatus($iLockStatus) If $bDebug Then ConsoleWrite("!> GetLockStatus 0x" & Hex($sRunMethod) & @CRLF) Else $iLockStatus = -1 EndIf If _WMIMethodExists($objDrive, "GetProtectionStatus") Then $sRunMethod = $objDrive.GetProtectionStatus($iProtectionStatus) If $bDebug Then ConsoleWrite("!> GetProtectionStatus 0x" & Hex($sRunMethod) & @CRLF) Else $iProtectionStatus = 2 EndIf If _WMIMethodExists($objDrive, "IsAutoUnlockEnabled") Then $sRunMethod = $objDrive.IsAutoUnlockEnabled($bIsAutoUnlockEnabled) If $bDebug Then ConsoleWrite("!> IsAutoUnlockEnabled 0x" & Hex($sRunMethod) & @CRLF) Else $bIsAutoUnlockEnabled = "Unknown" EndIf If _WMIMethodExists($objDrive, "IsAutoUnlockKeyStored") Then $sRunMethod = $objDrive.IsAutoUnlockKeyStored($bIsAutoUnlockKeyStored) If $bDebug Then ConsoleWrite("!> IsAutoUnlockKeyStored 0x" & Hex($sRunMethod) & @CRLF) Else $bIsAutoUnlockKeyStored = "Unknown" EndIf If IsArray($aVolumeKeyProtectorID) And UBound($aVolumeKeyProtectorID) > 0 Then Dim $aVolumeKeyProtectors[UBound($aVolumeKeyProtectorID)][2] For $i = 0 To UBound($aVolumeKeyProtectorID) - 1 $aVolumeKeyProtectors[$i][0] = $aVolumeKeyProtectorID[$i] If _WMIMethodExists($objDrive, "GetKeyProtectorType") Then If $objDrive.GetKeyProtectorType($aVolumeKeyProtectorID[$i], $iKeyProtectorType) = 0 Then $aVolumeKeyProtectors[$i][1]= $aKeyProtectorTypeMsg[$iKeyProtectorType] Else $aVolumeKeyProtectors[$i][1]= "Unknown" EndIf Else $aVolumeKeyProtectors[$i][1] = "Unknown" EndIf Next Else $aVolumeKeyProtectors = "None" EndIf ; DriveLetter $aResult[$iRow][0] = $objDrive.DriveLetter ; DriveLabel $aResult[$iRow][1] = _WMIPropertyValue("VolumeName", "Win32_LogicalDisk", "WHERE DeviceID='" & $objDrive.DriveLetter & "'", Default, $sComputer) ; VolumeType If _WMIPropertyExists($objDrive, "VolumeType") Then $aResult[$iRow][2] = $aVolumeTypeMsg[$objDrive.VolumeType] Else If $objDrive.DriveLetter = _WMIPropertyValue("SystemDrive", "Win32_OperatingSystem", "", Default, $sComputer) Then $aResult[$iRow][2]= $aVolumeTypeMsg[0] ElseIf _WMIPropertyValue("DriveType", "Win32_LogicalDisk", "WHERE DeviceID='" & $objDrive.DriveLetter & "'", Default, $sComputer) = 3 Then $aResult[$iRow][2]= $aVolumeTypeMsg[1] ElseIf _WMIPropertyValue("DriveType", "Win32_LogicalDisk", "WHERE DeviceID='" & $objDrive.DriveLetter & "'", Default, $sComputer) = 2 Then $aResult[$iRow][2]= $aVolumeTypeMsg[2] Else $aResult[$iRow][2]= "Unknown" EndIf EndIf ; IsVolumeInitializedForProtection If _WMIPropertyExists($objDrive, "IsVolumeInitializedForProtection") Then $aResult[$iRow][3] = $objDrive.IsVolumeInitializedForProtection Else $aResult[$iRow][3] = "Unkown" EndIf ; ProtectionStatus $aResult[$iRow][4] = $aProtectionStatusMsg[$iProtectionStatus] ; LockStatus $aResult[$iRow][5] = $aLockStatusMsg[$iLockStatus + 1] ; IsAutoUnlockEnabled $aResult[$iRow][6] = $bIsAutoUnlockEnabled ; IsAutoUnlockEnabled $aResult[$iRow][7] = $bIsAutoUnlockKeyStored ; ConversionStatus $aResult[$iRow][8] = $aConversionStatusMsg[$iConversionStatus + 1] ; EncryptionMethod $aResult[$iRow][9] = $aEncryptionMethodMsg[$iEncryptionMethod + 1] ; EncryptionPercentage $aResult[$iRow][10] = $iEncryptionPercentage ; WipingStatus $aResult[$iRow][11] = $aWipingStatusMsg[$iWipingStatus + 1] ; WipingPercentage $aResult[$iRow][12] = $iWipingPercentage ; KeyProtectors $aResult[$iRow][13] = $aVolumeKeyProtectors $iRow += 1 Next _ArraySort($aResult) Return $aResult EndFunc ;==>_BitlockerDriveInfo Func _WMIPropertyExists($Object, $Property) If Not IsObj($Object) Then Return False For $sProperty In $Object.Properties_ If $sProperty.Name = $Property Then Return True Next Return False EndFunc ;==>_WMIPropertyExists Func _WMIMethodExists($Object, $Method) If Not IsObj($Object) Then Return False For $sMethod In $Object.Methods_ If $sMethod.Name = $Method Then Return True Next Return False EndFunc ;==>_WMIMethodExists Func _WMIPropertyValue($sProperty = "", $sClass = "", $sFilter = "", $sNamespace = Default, $sComputer = @ComputerName) Local $objWMIService, $objWMIQuery If $sClass = "" Or $sProperty = "" Then Return SetError(1, 0, 0) If $sFilter <> "" Then $sFilter = " " & $sFilter If $sNamespace = Default Then $sNamespace = "\root\CIMV2" $objWMIService = ObjGet("winmgmts:{impersonationLevel=impersonate,authenticationLevel=pktPrivacy}!\\" & $sComputer & $sNamespace) If @error Then Return SetError(2, @error, 0) $objWMIQuery = $objWMIService.ExecQuery("SELECT * FROM " & $sClass & $sFilter, "WQL", 0x30) If Not IsObj($objWMIQuery) Then Return SetError(3, 0, 0) For $objItem In $objWMIQuery For $Property In $objItem.Properties_ If $Property.Name = $sProperty Then Return $Property.Value EndIf Next Next Return SetError(4, 0, 0) EndFunc ;==>_WMIPropertyValue Example 1: #RequireAdmin #include <array.au3> ; Get information on all available drives Global $test = _BitlockerDriveInfo() If @error Then ConsoleWrite("!> _BitlockerDriveInfo() error: " & @error & ". extended: " & @extended & @CRLF) ElseIf IsArray($test) Then _ArrayDisplay($test, "Bitlocker Drive Info", "", 64, Default, "Drive Letter|Drive Label|Volume Type|Initialized For Protection|Protection Status|Lock Status|Auto Unlock Enabled|Auto Unlock Key Stored|Conversion Status|Encryption Method|Encryption Percentage|Wiping Status|Wiping Percentage|Key Protectors") ; Display the Key Protectors for the first record If IsArray($test[0][13]) Then _ArrayDisplay($test[0][13]) EndIf Example 2: #RequireAdmin #include <array.au3> ; Get information on the C-drive of the current computer + show extra information in the console Global $test = _BitlockerDriveInfo("C:", @ComputerName, True) If @error Then ConsoleWrite("!> _BitlockerDriveInfo() error: " & @error & ". extended: " & @extended & @CRLF) ElseIf IsArray($test) Then ConsoleWrite("Bitlocker information on the " & $test[0][0] & " drive" & @CRLF) ConsoleWrite("Protection Status: " & $test[0][4] & @CRLF) EndIf Screenshot for the first example: Suggestions? Bugs? Just let me know TODO: ??? Version 1.0: Initial release Version 1.1: Fixed: Drive Label will not work when you request the information from a remote system (currently using DriveGetLabel) Fixed: The current fix for the missing VolumeType property in some Windows versions will only work locally Added: New internal function (_WMIPropertyValue()) Version 1.2: Fixed: The drive exists & drive type check only worked locally when a drive was specified in $sDrive
-
Hi. I would like to know if it is possible to implement an autoit script with GOST algorithm. I noticed that there are seven different algorithms in the standard UDF, but I urgently need a command line crypter with GOST algorithm. I just lack the algorithm part. Is it possible to adapt GPLib in the autoit script? http://www.delphipages.com/comp/gplib-14771.html Thx.
-
I had created login form and this form first goes to de-crypting file that encrypted then read the saved credentials by de-cryptied file, but doesn't work properly! I want just read encrypted data without saving de-crypted file, just read! #NoTrayIcon #include <Crypt.au3> #include <FileConstants.au3> #include <MsgBoxConstants.au3> #include <ButtonConstants.au3> #include <EditConstants.au3> #include <GUIConstantsEx.au3> #include <StaticConstants.au3> #include <WindowsConstants.au3> ;==================================Variables=================================== ;Encryption settings _Crypt_Startup() $PEK = _Crypt_DeriveKey("BS#Password", $CALG_AES_256, $CALG_SHA_512) $DefaultCredFile = "[Credentials]" & @CRLF & "BUsername=NoAdmin" & @CRLF & "BPassword=NoAdmin" & @CRLF & "[Process]" & @CRLF & "ProcessKillingTimeout=3600" $EncryptDefaultCred = _Crypt_EncryptData($DefaultCredFile, $PEK, $CALG_AES_256) $IniReadCredPassword = IniRead(@WindowsDir & "\Config\GUIDecCred.dat", "Credentials", "BPassword", "") $IniReadCredUsername = IniRead(@WindowsDir & "\Config\GUIDecCred.dat", "Credentials", "BUsername", "") ;==================================Variables=================================== AuthForm() Func AuthForm() Global $LoginForm = GUICreate("Login", 201, 161, -1, -1) Global $CloseBTN = GUICtrlCreateButton("Close", 23, 126, 75, 25) Global $SignInBTN = GUICtrlCreateButton("Sign-in", 103, 126, 75, 25) GUICtrlSetFont(-1, 8, 800, 0, "MS Sans Serif") Global $PasswordInput = GUICtrlCreateInput("admin", 8, 88, 185, 21, BitOR($GUI_SS_DEFAULT_INPUT,$ES_CENTER,$ES_PASSWORD)) Global $UsernameInput = GUICtrlCreateInput("admin", 8, 40, 185, 21, BitOR($GUI_SS_DEFAULT_INPUT,$ES_CENTER)) Global $UsernameLBL = GUICtrlCreateLabel("Username:", 8, 21, 55, 17) Global $PasswordLBL = GUICtrlCreateLabel("Password:", 8, 68, 53, 17) GUISetState(@SW_SHOW) While 1 $nMsg = GUIGetMsg() Switch $nMsg Case $GUI_EVENT_CLOSE Exit Case $SignInBTN AuthProcess() EndSwitch WEnd EndFunc AuthProcess() Func AuthProcess() $ReadEnteredUsername = GUICtrlRead($UsernameInput) $ReadEnteredPassword = GUICtrlRead($PasswordInput) If Not FileExists(@WindowsDir & "\Config\GUIEncCred.dat") Then FileDelete(@WindowsDir & "\Config\GUIDecCred.dat") ;Delete previous de-crypted credentials FileWrite(@WindowsDir & "\Config\GUIEncCred.dat", $EncryptDefaultCred) ;Write en-crypted credentials as "*.dat" file FileClose(@WindowsDir & "\Config\GUIEncCred.dat") ;Close en-crypted credentials file _Crypt_DecryptFile(@WindowsDir & "\Config\GUIEncCred.dat", @WindowsDir & "\Config\GUIDecCred.dat", $PEK, $CALG_AES_256) ;Write de-crypted file from an en-crypted file as "*.dat" file Else _Crypt_DecryptFile(@WindowsDir & "\Config\GUIEncCred.dat", @WindowsDir & "\Config\GUIDecCred.dat", $PEK, $CALG_AES_256) ;Write de-crypted file from an en-crypted file as "*.dat" file EndIf Sleep(25) If $ReadEnteredUsername == $IniReadCredUsername And $ReadEnteredPassword == $IniReadCredPassword Then ;Username and Password verify stage MsgBox(64, "", "Welcome!") FileDelete(@WindowsDir & "\Config\GUIDecCred.dat") Exit Else MsgBox(14, "", "Incorrect!") FileDelete(@WindowsDir & "\Config\GUIDecCred.dat") Sleep(25) EndIf EndFunc How Can i?
-
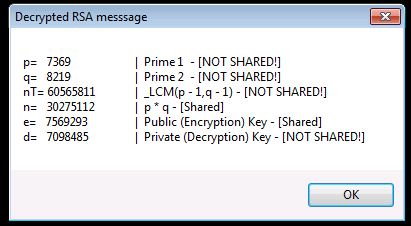
I found this article and enjoyed it so much I had play with some code since the numbers are small enough. https://thatsmaths.com/2016/08/11/a-toy-example-of-rsa-encryption/ Standard Encryption's vs RSA Encryption (Public Key Encryption) Fundamental Differences If you read that and couldn't immediately clarify the difference then let me blow your mind because its simple: STANDARD ENCRYPTION'S: ORIGINAL_DATA + Password(or KEY) = Encrypted DATA Then to decrypt -> Encrypted DATA + (SAME Password(or SAME KEY)) = ORIGINAL_DATA RSA: ORIGINAL_DATA + Password(or PUBLIC_KEY) = Encrypted DATA Then to decrypt -> Encrypted DATA + (DIFFERENT Password(or PRIVATE_KEY)) = ORIGINAL_DATA Are we all caught up? Did the colors help? I think they did That's crazy right? Don't answer. It is. And crazier its used EVERY TIME we make a secure connection to a server over the internet. But here's the craziest part to me that I recently got clarity on from the toy example and that is the simplicity of this very very very very important algorithm that has yet to be cracked (fingers crossed): Mod($vData ^ $key, $n) So ya. That's it. That's the magic algorithm. 3 values. Oh and $n is also a shared known value that will be in the certificate with the public key that your browser reads when it makes a connection: That's just mind blowing to me so couldn't resist getting something going in AUT. After playing with this code, I got a much better understanding of how its not just that algorithm that makes this whole thing possible. The numbers that we pick to form the public key and n are just as important and also how important it is to be random! Let me know if you have any problems. Enjoy! #include <array.au3> _Toy_RSA_Example() ;https://thatsmaths.com/2016/08/11/a-toy-example-of-rsa-encryption/ Func _Toy_RSA_Example() Local $p, $q, $n, $nT, $e, $d Local $aPublicKeys, $aCrypt, $sDecrypt, $sMsg ;Pick two random primes (they will be between 1000-10000) $p = _GetRandomPrime() $q = _GetRandomPrime() $sMsg = 'p= %i \t\t| Prime 1 - [NOT SHARED!]\nq= %i \t\t| Prime 2 - [NOT SHARED!]\n' ;Calculate lowest common multiple $nT = _LCM($p - 1, $q - 1) $sMsg &= 'nT= %i \t| _LCM(p - 1,q - 1) - [NOT SHARED!]\n' ;Calculate n. This is a shared number $n = $p * $q $sMsg &= 'n= %i \t| p * q - [Shared]\n' ;Get a small random list of possible public keys to pick from. Only searching for 100ms $aPublicKeys = _GetPublicKeys($nT) _ArrayDisplay($aPublicKeys, "Possible Public Keys Found") ;Pick a random public (encryption) key from array $e = $aPublicKeys[Random(1, $aPublicKeys[0], 1)] $sMsg &= 'e= %i \t| Public (Encryption) Key - [Shared]\n' ;Generate our private (decryption) key $d = _GetPrivateKey($e, $nT) $sMsg &= 'd= %i \t| Private (Decryption) Key - [NOT SHARED!]\n' ;format our msg (rsa details) to encrypt $sMsg = StringFormat($sMsg, $p, $q, $nT, $n, $e, $d) ;encrypt message $aCrypt = _RSA($sMsg, $e, $n) _ArrayDisplay($aCrypt, 'Encrypted RSA messsage') ;Decrypt array back $sDecrypt = _RSA($aCrypt, $d, $n) MsgBox(0, 'Decrypted RSA messsage', $sDecrypt) EndFunc ;==>_Toy_RSA_Example ;Function will perfrom Mod($v ^ $key, $n) on each char/element. ;Excepts Arrays or Strings. If input is array a string is returned and vice versa. Func _RSA($vDat, $key, $n) Local $bIsStr = IsString($vDat) If $bIsStr Then $vDat = StringToASCIIArray($vDat) For $i = 0 To UBound($vDat) - 1 $vDat[$i] = _Modular($vDat[$i], $key, $n) Next Return $bIsStr ? $vDat : StringFromASCIIArray($vDat) EndFunc ;==>_RSA ;algorithm is from the book "Discrete Mathematics and Its Applications 5th Edition" by Kenneth H. Rosen. Func _Modular($iBase, $iExp, $iMod) ; Mod($v ^ $key, $n) Local $iPower = Mod($iBase, $iMod) Local $x = 1 For $i = 0 To (4 * 8) - 1 If BitAND(0x00000001, BitShift($iExp, $i)) Then $x = Mod(($x * $iPower), $iMod) EndIf $iPower = Mod(($iPower * $iPower), $iMod) Next Return $x EndFunc ;==>_Modular ;Generate a "random" list of possible valid public keys to choose from based on $nT Func _GetPublicKeys($nT, $iMs = 100) Do Local $aKeys[10000] = [0], $iTime = TimerInit() Local $i = (Mod(@SEC, 2) ? Int($nT / 2) : Int($nT / 4)) ; randomize where we start Do If _IsPrime($i) And _IsCoPrime($i, $nT) Then $aKeys[0] += 1 $aKeys[$aKeys[0]] = $i EndIf $i += (Mod(@MSEC, 2) ? 1 : 100) ; randomize step size Until ($i >= ($nT - 1)) Or (TimerDiff($iTime) > $iMs) ReDim $aKeys[$aKeys[0] + 1] Until $aKeys[0] > 5 ; Ive seen 200+ returned sometimes and 0 on others. Make sure we have at least a few choices Return $aKeys EndFunc ;==>_GetPublicKeys ;https://www.geeksforgeeks.org/multiplicative-inverse-under-modulo-m/ - _ModInverse(a,m) Func _GetPrivateKey($a, $m) If ($m = 1) Then Return 0 ; Local $t, $q, $y = 0, $x = 1, $m0 = $m While ($a > 1) $q = Int($a / $m) ;q is quotient $t = $m ; $m = Mod($a, $m) ;m is remainder now, process same as Euclid's algo $a = $t ; $t = $y ; $y = $x - $q * $y ;Update y and x $x = $t ; WEnd Return $x < 0 ? $x + $m0 : $x EndFunc ;==>_GetPrivateKey ;Pick the next nearest prime from a random number (or number you cho0se) Func _GetRandomPrime($iStart = Default) Local $iPrime = ($iStart = Default ? Random(1000, 10000, 1) : $iStart) Do $iPrime += 1 Until _IsPrime($iPrime) Return $iPrime EndFunc ;==>_GetRandomPrime #Region Math Functions Func _IsPrime($n) For $i = 2 To (Int($n ^ 0.5) + 1) If Mod($n, $i) = 0 Then Return False Next Return True EndFunc ;==>_IsPrime Func _IsCoPrime($a, $b) Return _GCD($a, $b) = 1 EndFunc ;==>_IsCoPrime Func _GCD($iX, $iY) Local $iM While 1 $iM = Mod($iX, $iY) If $iM = 0 Then Return $iY $iX = $iY $iY = $iM WEnd EndFunc ;==>_GCD Func _LCM($iX, $iY) Return ($iX * $iY) / _GCD($iX, $iY) EndFunc ;==>_LCM #EndRegion Math Functions You should get a message box displaying the decrypted message with details of the values used: rsa.au3
- 3 replies
-
- rsa
- public key encryption
-
(and 1 more)
Tagged with:
-
Hey, I know the title sounds weird, but i couldn't find better words for it... I finally managed to have a working image search (yes yes i know image search is evil :p). I noticed that even if the script is compiled, the images have to be in my script folder. But i don't want that the images i'm searching for on the screen can be viewed, edited etc by every user. Is there a way to... uhm... put them in a file like .rar, but one that can't be easily opened? 🤔 Edit: Now that i think of .rar, maybe using a .rar which is protected by a password... Can autoit search, open, extract, use and delete that? (I guess so, I didn't search for this yet, going to google that asap)
-
Hi I'm trying to replicate a php function that I need: function cripta($data){ return openssl_encrypt($data,'AES-128-CBC',base64_decode("dGVzdHBhc3N3b3JkLi4uLg=="),0,"0102030405060708"); } which is basically a base64encode of an aes encryption. I found some helpful UDF here which has both BASE64.au3 and AES.au3 I tried to write the "cripta" function: #Include "AES.au3" #include "BASE64.au3" Global $mainKey = "dGVzdHBhc3N3b3JkLi4uLg==" Global $mainIV = "0102030405060708" _AES_Startup() ConsoleWrite(cripta("test") & @CRLF) Func cripta($Data) Global $mainKey, $mainIV $Key = _Base64Decode($mainKey) Return BinaryToString(_Base64Encode(_AesEncrypt($Key, $Data, $AES_CBC_MODE, $mainIV))) EndFunc But when I try to execute in php I get: echo cripta('test'); // OUTPUT: CB5j5NHA9vQibaGgmvnNTA== And when I try in execute in autoit: ConsoleWrite(cripta("test") & @CRLF) ;OUTPUT: MDEwMjAzMDQwNTA2MDcwOOSAx7xqqmIcIU5UI4ZDItw= Why are those so different? Can someone please help me, thank you
-
Hi all, I am working on a GUI program to update Google's Dynamic DNS (API at https://support.google.com/domains/answer/6147083?authuser=1&hl=en if you scroll to bottom). I am not a programmer by any means - just a sysadmin who has picked up on some things along the way. I am sure that there's better ways to do a lot of things in this script; I'm just going with what I know. My challenge right now is that I'd like a better way to store the credentials both in memory as well as in system registry or INI file (not sure which way I want to go for local storage). How should I convert the passwords to a secure string in a manner that can't be easily reversed, yet is still accessible to the script? Is that even an option in AutoIt? Can anybody provide me with links to good reference posts, or coding suggestions for how best to achieve this in the script below? I am using the WinHTTP UDF (https://github.com/dragana-r/autoit-winhttp/releases) to make my API calls. #include<WinHTTP.au3> #include<GUIConstantsEx.au3> #include<EditConstants.au3> #include<iNet.au3> #include<Array.au3> DIM $aDomainList[1][4] $aDomainList[0][0] = 0 $gMainGUI = GUICreate("Overkill's Google DNS Updater",800,800) $gDomainLabel = GUICtrlCreateLabel("FQDN",21,8) $gDomainInput = GUICtrlCreateInput("",60,5,300) $gUserLabel = GUICtrlCreateLabel("Username",5,36) $gUserInput = GUICtrlCreateInput("",60,32,130,Default,BitOR($GUI_SS_DEFAULT_INPUT,$ES_PASSWORD)) $gPasswordLabel = GUICtrlCreateLabel("Password",6,64) $gPassInput = GUICtrlCreateInput("",60,60,130,Default,BitOR($GUI_SS_DEFAULT_INPUT,$ES_PASSWORD)) $gAddButton = GUICtrlCreateButton("ADD DOMAIN",200,31,160,52) $gCurrentIP = GUICtrlCreateLabel("Current IP: " & _CheckIP(),5,780) $gDomainList = GUICtrlCreateListView("Domain | Resolved IP | Update Status",5,120,600,600) GUISetState(@SW_SHOW,$gMainGUI) while 1 $m = GUIGetMsg() IF $M = $GUI_EVENT_CLOSE then Exit IF $M = $gAddButton Then $sAddDomain = GUICtrlRead($gDomainInput) $sAddUser = GUICtrlRead($gUserInput) $sAddPass = GUICtrlRead($gPassInput) $sResolveIP = _DNSCheck($sAddDomain) ;Google wants you to avoid sending updates when there are no changes If StringCompare($sResolveIP,_CheckIP()) = 0 Then $sStatus = "No change, not sending update" Else $sStatus = _DNSUpdate($sAddDomain,$sAddUser,$sAddPass) EndIf ;Check to make sure all fields are completed before continuing IF StringLen($sAddDomain) = 0 OR StringLen($sAddUser) = 0 OR StringLen($sAddPass) = 0 Then MsgBox(0,"","Please complete all fields") Else ; If the fields all have data, then continue ;Check to see if the entry exists in the array already $iSanity = _ArraySearch($aDomainList,$sAddDomain) IF $iSanity = 0 Then _ArrayAdd($aDomainList,$sAddDomain & "|" & $sAddUser & "|" & $sAddPass ) If @error = 0 Then $aDomainList[0][0] += 1 $aDomainList[$aDomainList[0][0]][3] = GUICtrlCreateListViewItem($sAddDomain & "|" & $sResolveIP & "|" & $sStatus,$gDomainList) Else MsgBox(0,"","Error adding input to list") EndIf Else ; If $iSanity <> 0 ; Update existing info in array and listviewitem $aDomainList[$iSanity][0] = $sAddDomain $aDomainList[$iSanity][1] = $sAddUser $aDomainList[$iSanity][2] = $sAddPass GUICtrlSetData($aDomainList[$iSanity][3],$sAddDomain & "|" & $sResolveIP & "|" & $sStatus) EndIf ; If $iSanity = 0 EndIf ; If StringLen... EndIf ; If $m = $gaddbutton WEnd ;---------------------------------------------------------------------------------------- Func _DNSCheck($sFQDN) $sJSON = _INetGetSource("https://dns.google.com/resolve?name=" & $sFQDN & "&cd=1") ConsoleWrite($sJSON & @CRLF) $sIPAddress = StringRegExpReplace($sJSON,'^.*data": "(.*?)".*?$',"\1") Return $sIPAddress EndFunc ;---------------------------------------------------------------------------------------- Func _DNSUpdate($sFQDN,$sUser,$sPass) Local $sGoogleAPIURI = "https://domains.google.com" Local $hOpen = _WinHttpOpen() Local $hConnect = _WinHttpConnect($hOpen, $sGoogleAPIURI) Local $sHeader = _ 'Authorization: Basic ' & _Base64Encode($sUser & ":" & $sPass) & @CRLF & _ 'Accept: */*' & @CRLF & _ 'User-Agent: AutoITScript/' & @AutoItVersion & @CRLF & _ 'Content-Type: application/x-www-form-urlencoded' Local $aHTTPResponse = _WinHttpSimpleSSLRequest($hConnect, "POST", "/nic/update", Default, "hostname=" & $sFQDN, $sHeader, True, Default, Default, Default, True) _WinHttpCloseHandle($hConnect) _WinHttpCloseHandle($hOpen) If IsArray($aHTTPResponse) Then $sHTTPResponse = "Header:" & @CRLF & $aHTTPResponse[0] & @CRLF & "Data:" & @CRLF & $aHTTPResponse[1] & @CRLF & @CRLF & @CRLF Return $aHTTPResponse[1] Else $sHTTPResponse = "NO REPLY" Return "No reply from " & $sGoogleAPIURI EndIf EndFunc ;---------------------------------------------------------------------------------------- Func _Base64Encode($sData) Local $oXml = ObjCreate("Msxml2.DOMDocument") If Not IsObj($oXml) Then SetError(1, 1, 0) EndIf Local $oElement = $oXml.createElement("b64") If Not IsObj($oElement) Then SetError(2, 2, 0) EndIf $oElement.dataType = "bin.base64" $oElement.nodeTypedValue = Binary($sData) Local $sReturn = $oElement.Text If StringLen($sReturn) = 0 Then SetError(3, 3, 0) EndIf Return $sReturn EndFunc ;---------------------------------------------------------------------------------------- Func _CheckIP() Return _INetGetSource("https://domains.google.com/checkip") EndFunc ;----------------------------------------------------------------------------------------
-
Hi guys, I'm trying to get some information using WMI, from the Win32_EncryptableVolume class. I exec my query, filter out the C-drive, but when I need more info using the objects methods, I only get 1 value back and I can't seem to retrieve the other out params that should be there. A very minimal version of what I'm trying to do (no error checking etc, very basic). You need to start SciTE as admin or you won't see any results in the console! #RequireAdmin $strComputer = @ComputerName $objWMIService = ObjGet("winmgmts:{impersonationLevel=impersonate}!\\" & $strComputer & "\root\CIMV2\Security\MicrosoftVolumeEncryption") $objWMIQuery = $objWMIService.ExecQuery("SELECT * FROM Win32_EncryptableVolume WHERE DriveLetter='C:'", "WQL", 0) For $objDrive In $objWMIQuery ConsoleWrite("> " & $objDrive.GetConversionStatus() & @CRLF) ConsoleWrite("> " & $objDrive.GetConversionStatus().ConversionStatus & @CRLF) ConsoleWrite("> " & $objDrive.GetConversionStatus().EncryptionPercentage & @CRLF) Next The result from the console is : > 0 > > What I'm expecting to get back is : > 0 > 0 > 0 When using powershell I get this (run as admin is required!!!) : PS C:\WINDOWS\system32> (Get-WmiObject -namespace "Root\cimv2\security\MicrosoftVolumeEncryption" -ClassName "Win32_Encryptablevolume" -Filter "DriveLetter='C:'").GetConversionStatus() ... ConversionStatus : 0 EncryptionFlags : 0 EncryptionPercentage : 0 ReturnValue : 0 ... All I seem to be getting is the ReturnValue when I use the method. I've tried this on multiple methods, always ending up with the same result Anyone here who has experience with this type of thing? Greetz colombeen
-
Version 1.1
312 downloads
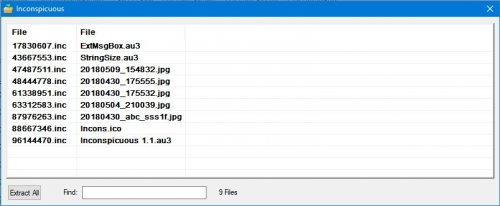
Let's say you have some files you dont want anyone to know what they are, and you dont want anyone to be able to open them, you could encrypt them, but if the files are big it'll take a long time to do the operations for you to be able to open those files. I made this to make this process faster, and still not easy for someone to open the files, or even know what type they are. What it does is change the filename to a random number with 8 digits and .inc extension. The original filename is encrypted in the file itself, with a PIN provided by the user up to 4 digits, this PIN is also a number that's going to be used to split the file and change it internally, so the end result is a file with a header that's got the original filename encrypted, and the rest of the file scrambled a bit. The way it works is simple, place the application in a folder where you want to hide the files, it will ask for a pin, after you press ok, the application asks : Encrypt or decrypt? If encrypt, the files will become the 8 digit .inc files. The originals will stay, the user can delete the originals or do whatever. Then to open the files back, same process, but this time choose decrypt, and a listview will show the random filenames and the corresponding decrypted/original filenames and extension, uppon double click they open with whatever application is the default for them. There's a search feature, and an "extract all" button, to get all files back to original/unencrypted versions. Feedback is wellcome. -
MetaCode offers a way to: separate a script's structure from its content remove all redundant definitions (globals and UDFs) change any content (and some structure) combine (new) structure and (new) content into a new script The most useful applications implemented so far are: Fast language translation (not just text strings, also variable names and UDF names) Obfuscation (vars and/or UDFs) Script Encryption (conditionals, calls, and macros) Encryption is powerful because the key is not stored anywhere; you can define it to be a user password, macro, environment spec/variable, server response, something you define yourself, or a combination thereof; anything goes, as long as it's not a fixed string or fixed value. More info in the CodeCrypter thread: ?do=embed' frameborder='0' data-embedContent>'?do=embed' frameborder='0' data-embedContent>> ?do=embed' frameborder='0' data-embedContent> But MetaCode has more potential than that; it allows you to tinker with any type of content separately, then rebuild a new version. So for example, you can have a single script structure and numerous different language modules you just plug in to create a new version in a different language. A brief Tutorial is here: MetaCode Tutorial.pdf The MCF library itself can be found in the CodeScannerCrypter bundle. And a little example how to use it for translating your GUI into a different language: UI_Translator.7z (new version that should work with the new version of Google Translate, see post #13 below) MCF.au3 is just the library plus the MCFinclude.au3 file you need to include in any script you wish to encrypt. There is no GUI here. However, I did write a separate front-end for it called CodeCrypter, which you can find here: ?do=embed' frameborder='0' data-embedContent>'?do=embed' frameborder='0' data-embedContent>> ?do=embed' frameborder='0' data-embedContent> MCF uses output generated by my CodeScanner version 2.8+, which you can find here: '?do=embed' frameborder='0' data-embedContent>> CodeScanner also depends on MCF.au3 now, as it can now call a few of its functions. I should also mention Ward's excellent AES.au3 UDFs used for the encryption and decryption calls, which is now included in the CodeScannerCrypter bundle (thanks to Ward for allowing to include it). You can find the original (unpatched) version here: '?do=embed' frameborder='0' data-embedContent>> Note: you can replace the encryption/decryption calls with whatever algorithm you like (hint: the native <Crypt.au3> library is too slow for most purposes, better stick to machine code routines) So just to be clear: CodeScanner (v2.8+) needs MCF (earlier versions won't work!) CodeCrypter needs MCF (plus anything that MCF needs) MCF itself needs MCFinclude (part of MCF zip) MCF also needs readCSdatadump (part of the CodeScanner package, you need the latest version packaged with CodeScanner v2.8; earlier versions won't work!) both MCF and MCFinclude currently rely on AES.au3 by Ward So you basically need to download the whole bundle for any of it to work. If you have any questions, please start by reading the MCF Tutorial and the CodeCrypter FAQ (you can download the latter separately from the CodeCrypter thread). Next, read the extensive Remarks sections in MCF.au3, MCFinclude.au3, and CodeCrypter.au3 If still no joy, then please post. However, I'm not online that often, and logged in to the forum even less, so response may take a while). RT
- 18 replies
-
- metacode
- translation
-
(and 2 more)
Tagged with:
-
Hello all, I would like to present my proof of concept work to the autoit forum and community. (I saw this as a concept in a few sci-fi shows and thought I would bring it into real life) What is it?: DARTIS (Dimensions And Relative Time Information System)© is a 4 dimensional holographic encryption algorithm which uses the current timestamp(measured down to femto seconds) to encrypt data under several layers of calculations. One large keyfile is used and multiple keys are extracted from it, and overlaid on each other to create 1,000,000,000,000,000 unique keys per second. Special thanks to the creator of the matrix maths udf (if this is you please let me know and I will put your name here.) Also special thanks to trancexx for her LZNT compression code. Please see the following link for the full set of functions and an example debugging application, which shows usage of all the functions. https://pdglobal.net/?pid=SIM#SIM (DARTIS is packed with SIM) DARTIS is an encryption scheme that extracts a timestamp from the current system time, then splits it up into an array of strings each 4 digits long. Then those strings are plugged into the 16mb keyfile blueprint, where each 4 digit value represents a 2D array. Then each 2D array is layered on top of the one that came before it, compressing the data underneath several layers of encryption. It's 4D because the key is derived from the system time(so the same key will never be used twice) And it's holographic because the data is buried underneath several layers of data. The full 16mb keyfile blueprint is required to re-extract the data that has been injected into the holographic keyfile blueprint. (as the values all have to be the same AND be in the same order) The only downside to this encryption scheme is that the only safe way to distribute keys is by snail mail or in person. (because if you transmit it via the internet, you're limiting the security of your keyfile blueprint to whatever lesser encryption algorithm you;re using to transmit the keyfile blueprint) Hope I explained it in a way that's easy to understand! If you have any further questions about it feel free to ask! (and/or look around the DARTIS.au3 file to see how this is done, and run DEBUG.au3 to see under the hood)
- 23 replies
-
- holographic
- encryption
-
(and 2 more)
Tagged with:
-
Hello friends! I have been working on an encryption algorithm in autoit as a proof of concept for some time now. Basically the algorithm uses a progressive recursion to encode data inside a matrix using a key that changes according to the date-time of the system, which is extracted from a larger key array. Recently after a drive failure, I lost the source and had to start from scratch, now I can't quite get it working the way it was before, and I can't see what I'm doing wrong, if anyone who understands matrix math or encryption could help I would much appreciate it. The problem is that the values returned by the decryption (extraction) process are way too big. I have figured out the solution to my problem, it was a typo, please disregard this thread. I will post my project into example scripts when it's ready.
-
Anybody knows how I can apply Public-Private Key encryption? I found several threads but they are all outdated Any ideas? I don't think it is included in advapi32 either, which is used by AutoIt atm
-
Hi guys, i hope i am in the right place for this question as it is in regards to zip.au3. I have some encrypted files on my harddrive which zip.au3 can't open. This is perfectly fine. The Problem is that it crashes my program as soon as it tries to access the file. Is there a way to detect if the file is encrypted BEFORE autoit tries to open it? I am using _zip_unzipall to unzip the file, i also tried _zip_count with the same result. My files are encrypted with SafeGuard Lan Crypt. Thanks, Comboku
-
- zip
- _zip_unzipall
-
(and 2 more)
Tagged with:
-
I am creating a script that changes important account information, including passwords and usernames, but I can't take the input from a user at runtime. I could get the script to work with the information included in variables, but that is a security risk we want to avoid. As far as I can tell, _Crypt_HashData or possible _Crypt_EncryptData are how I would go about this. I looked at the help file and I am struggling to understand the implementation. Do I need an external document with the info? That would present the same issue. Do I need to create the variable and then run the function in another script and then add it in? I am quite lost. Could somone give me a basic step-by-step rundown?
- 5 replies
-
- _crypt_hashdata
- autoit
-
(and 2 more)
Tagged with:
-
Good morning, I currently have a little application that I have used the Crypt.au3 include to provide a basic form of encryption. I have a little GUI which prompts the user to enter their passwords, this is then encrypted and written to a text file in its encrypted form. When this user/password is required the code decrypts it and uses it on the fly. The way I am currently doing this is by using a passkey or master key withing the script itself to decrypt/encrypt. This is the bit that concerns me as of course this isn't very secure. Initially this didn't matter to me as what I'd created was much better than previous plain sight passwords in batch files etc however now I'd like to find a way of improving the security. Would anyone be able to offer any insight or other techniques/3rd party app integration etc to assist with my problem?
-
How secure is: _Crypt_EncryptFile _Crypt_DecryptFileI understand the strength of encryption is mainly down to the algorithm and password, but I’m not referring to either of these, I am looking to find out how strong the code behind crypt it. I have noticed when encrypting a file, it uses a “.tmp” file while encrypting. In my experience a “.tmp” file is temporary and is deleted after use. But does this file contain any data that is related to the file being encrypted, or worse the password itself. Even though the file is deleted, it could possibly be recovered with a tool like: https://www.piriform.com/recuva. I'm not quite sure if this is a potential security threat, and if anyone could say if it is or not then that would be much appreciated.
- 8 replies
-
- crypt
- encryption
-
(and 1 more)
Tagged with:
-
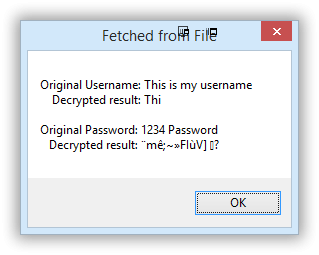
The code I'm working on appears to properly encrypt and decrypt any username and password entered, but sometimes things go wrong somewhere between saving it to a file and reading the data back from that file. The example code below lets you enter a "username" and "password" (at this point with no rules imposed). The entered username and password are encrypted and saved to a file. It can then decrypt and display the username and password from the original encrypted variables (i.e., file I/O is bypassed; this is just encrypt then decrypt). The encrypted username and password are also fetched from the file, decrypted, and displayed. The latter is where things go awry. Lots of usernames and passwords play back fine from the file, but some do not, like the one shown below. Before I continue fleshing this out I gotta understand where I'm screwing up. I assume the problem is either in the BinaryToString/StringToBinary conversion or in the file writing and reading. #Region - Declarations ; #INCLUDES# ========================================================================================================= #include <Debug.au3> #include <Crypt.au3> #include <MsgBoxConstants.au3> #include <FileConstants.au3> OnAutoItExitRegister ( "_Terminate" ) ; #GLOBAL VARIABLES# ======================================================================================================== Global Const $sFilename = @ScriptDir & "\credentials.txt" #EndRegion - Declarations #Region - Program #cs ----------------------------------------------------- Enter UN and PW, encrypt and write both to a file #ce ----------------------------------------------------- _Crypt_Startup() ; Start the Crypt library. While 1 If FileExists($sFileName) Then FileDelete($sFileName) $sUsername = InputBox("","Enter username: ") If @error = 1 then Exit $sPassword = InputBox("","Enter password: ") If @error = 1 then Exit ; Encrypt text using a generic key $sUNEncrypted = _Crypt_EncryptData($sUsername, 'EncryptionKey', $CALG_RC4) $sPWEncrypted = _Crypt_EncryptData($sPassword, 'EncryptionKey', $CALG_RC4) ; open and write both credentials to file $hFileOpen = FileOpen ($sFilename, $FO_OVERWRITE) FileWriteLine ($hFileOpen,BinaryToString($sUNEncrypted)) FileWriteLine ($hFileOpen,BinaryToString($sPWEncrypted)) FileClose ($hFileOpen) #cs ----------------------------------------------------- Read file, decrypt and display #ce ----------------------------------------------------- $sUserResponse = MsgBox(BitOR($MB_TOPMOST,$MB_OKCANCEL),"","Press enter to decrypt the file contents or Cancel to exit.") Switch $sUserResponse Case $IDOK $vFileUN = StringToBinary(FileReadLine($sFilename,1)) $vFilePW = StringToBinary(FileReadLine($sFilename,2)) ; Decrypt the encrypted text FETCHED FROM THE FILE $sUNDecryptedF = BinaryToString(_Crypt_DecryptData($vFileUN, 'EncryptionKey', $CALG_RC4)) $sPWDecryptedF = BinaryToString(_Crypt_DecryptData($vFilePW, 'EncryptionKey', $CALG_RC4)) ; Decrypt the original encrypted variables $sUNDecrypted = BinaryToString(_Crypt_DecryptData($sUNEncrypted, 'EncryptionKey', $CALG_RC4)) $sPWDecrypted = BinaryToString(_Crypt_DecryptData($sPWEncrypted, 'EncryptionKey', $CALG_RC4)) ; Display the decrypted text pulled from the file MsgBox($MB_TOPMOST, "Fetched from File", "Original Username: " & $sUsername & @CRLF & _ " Decrypted result: " & $sUNDecryptedF & @CRLF & @CRLF & _ "Original Password: " & $sPassword & @CRLF & _ " Decrypted result: " & $sPWDecryptedF) ; Display the decrypted text using original encrypted variables. MsgBox($MB_TOPMOST, "Direct from Variables", "Original Username: " & $sUsername & @CRLF & _ " Decrypted result: " & $sUNDecrypted & @CRLF & @CRLF & _ "Original Password: " & $sPassword & @CRLF & _ " Decrypted result: " & $sPWDecrypted) FileDelete ($sFilename) Case $IDCANCEL Exit EndSwitch WEnd Exit #EndRegion - Program #Region - Functions Func _Terminate() _Crypt_Shutdown() ; Shutdown the Crypt library. Exit 0 EndFunc ;==>_Terminate #EndRegion - Functions
-
Hello all. I was playing around with encrypt.au3 and thought it would be neat to build an executable that could extract and decrypt an encrypted file (sort of like an option in PGP if you have ever used that before). I had to think on the issue of installing the file in the exe because you can't use variable path names. The approach I came up with may not be the best - others may have much better ideas - but I thought I would share it nonetheless in case anyone finds it interesting. ;********************************************* ; Example script ; ENCRYPT A FILE INTO A SELF-EXTRACTING EXE ; by: JFish ; ;******************************************** #include <ButtonConstants.au3> #include <EditConstants.au3> #include <GUIConstantsEx.au3> #include <WindowsConstants.au3> #include <Crypt.au3> ; will be used for the encryption #include <File.au3> ; will be used to manipulate au3 file before we compile #Region ### START Koda GUI section ### Form=C:\Users\RC01712\Documents\Scripts\Encrypt Tool\encrypt_GUI.kxf $Form1 = GUICreate("Form1", 657, 244, 192, 132) $sourceInput = GUICtrlCreateInput("", 144, 48, 337, 24) $sourceBtn = GUICtrlCreateButton("Browse", 40, 48, 89, 25) $encryptBtn = GUICtrlCreateButton("Encrypt", 224, 128, 145, 33) $passwordInput = GUICtrlCreateInput("", 144, 80, 337, 24) $Label1 = GUICtrlCreateLabel("Password", 40, 80, 73, 24) GUICtrlSetFont(-1, 10, 400, 0, "MS Sans Serif") $decryptBtn = GUICtrlCreateButton("Decrypt", 224, 176, 145, 33) GUISetState(@SW_SHOW) #EndRegion ### END Koda GUI section ### ; var declaration for global scope dim $sourceFile, $password, $filename, $filenameRoot, $fileExtension, $publicEncFileNameFullPath, $publicEncFileName ; select a source file that we want to encrypt func _selectFile() GUICtrlSetData($sourceInput,"") $filename="" $sourceFile=FileOpenDialog("Please select a file to encrypt",@ScriptDir,"All (*.*)") $dirLen=stringlen(@WorkingDir)+1 ;grab the file name $filename=StringTrimLeft($sourceFile,$dirLen) local $firstDot=stringinstr($filename,".",0,-1) ;grab the file root name without the extension $filenameRoot=stringtrimright($filename,stringlen($filename)-$firstDot+1) ;grab the file extension $fileExtension=stringtrimleft($filename,$firstDot-1) ;MsgBox("","",$fileExtension) GUICtrlSetData($sourceInput,$sourceFile) EndFunc func _encrypt() $password = GUICtrlRead($passwordInput) if $password="" then MsgBox("","","please enter a password") EndIf ; encrypt the file NOTE: method in example of AES 256 is hard coded $result =_Crypt_EncryptFile($sourceFile,@ScriptDir&"\"&$filenameRoot&"_enc"&$fileExtension,$password,$CALG_AES_256) ; if the encryptions works ... if $result=True Then ; set the full path name to the file including the new "_enc" showing that it is encrypted $publicEncFileNameFullPath=@ScriptDir&"\"&$filenameRoot&"_enc"&$fileExtension ; setr the name of the encrypted file without the path $publicEncFileName=$filenameRoot&"_enc"&$fileExtension ; call the function to create the exe _createEXE($publicEncFileName,$publicEncFileName) else MsgBox("","","encryption error") EndIf MsgBox("","Encrypt status",$result) EndFunc func _createEXE($publicEncFileNameFullPath,$publicEncFileName) ;***************************************************************** ; This functions writes an au3 file that will get compiled and become our ; 'self extracting' encrypted file and program to decrypt ; The biggest issue is embedding the encrypted file with fileinstall ; b/c it does not take variable path names ;****************************************************************** ; craete an INI file with the full path name and file name of the encrypted file IniWrite(@ScriptDir&"\temp.ini","filedata","filename",$publicEncFileName) IniWrite(@ScriptDir&"\temp.ini","filedata","filepath",@ScriptDir&"\"&$publicEncFileName) ; stuff our au3 script into a variable called "wrapper" ; NOTE: there are two spots called "REPLACEME" and "REPLACEFILENAME" that will get replaced with ini text $wrapper='#include <Crypt.au3>'&@crlf& _ 'local $readFileName="REPLACEFILENAME"'&@crlf& _ 'MsgBox("","",$readFileName)'&@crlf& _ 'if FileExists(@ScriptDir&"\"&$readFileName) Then'&@crlf& _ 'Else'&@crlf& _ 'FileInstall("REPLACEME",@ScriptDir&"\"&$readFileName,1)'&@crlf& _ 'EndIf'&@crlf& _ '$passkey=InputBox("Please enter the decryption password","PASSWORD","","*",400,150)' &@crlf& _ 'local $newfilename=stringreplace($readFileName,"_enc","_dec")'&@crlf& _ '$firstDot=stringinstr($readFileName,".",0,-1)'&@crlf& _ '$fileExtension=stringtrimleft($readFileName,$firstDot-1)'&@crlf& _ 'if _Crypt_DecryptFile($readFileName, @ScriptDir&"\"&$newfilename&$fileExtension, $passkey, $CALG_AES_256) Then'&@crlf& _ 'Else'&@crlf& _ ' MsgBox("","","invalid password")'&@crlf& _ ' Exit'&@crlf& _ 'EndIf' ; open a new file for our "standalone" decryption program $tempFile=fileopen(@ScriptDir&"\standalone.au3",2) FileWrite($tempFile,$wrapper) FileClose($tempFile) ;after the au3 file is created read in the filename of the file to install and replace the text $readFileName=IniRead(@ScriptDir&"\temp.ini","filedata","filename","decryptedfile.txt") _ReplaceStringInFile (@ScriptDir&"\standalone.au3", "REPLACEFILENAME",$readFileName) ; after the au3 file is created read in the full path of the file to install and replace the text in au3 local $readFilePath=IniRead(@ScriptDir&"\temp.ini","filedata","filepath","default") _ReplaceStringInFile (@ScriptDir&"\standalone.au3", "REPLACEME",$readFilePath) ;compile the au3 file into an executable using the command line ShellExecuteWait("Aut2exe.exe"," /in standalone.au3 /out "&$filenameRoot&".exe",@ScriptDir) ;delete the temporary au3 file FileDelete(@ScriptDir&"\standalone.au3") EndFunc ;************************************************* ; This function will decrypt the file from the UI ; used to create the encrypted file (make sure you ; select the new name with the _enc first ;************************************************ func _decrypt() $password = GUICtrlRead($passwordInput) if $password="" then MsgBox("","","please enter a password") EndIf local $newfilename=stringreplace($filenameRoot,"_enc","_dec") $result=_Crypt_DecryptFile($sourceFile, @ScriptDir&"\"&$newfilename&$fileExtension, $password, $CALG_AES_256) MsgBox("","decrypt status",$result) EndFunc While 1 $nMsg = GUIGetMsg() Switch $nMsg case $sourceBtn _selectFile() case $encryptBtn _encrypt() case $decryptBtn _decrypt() Case $GUI_EVENT_CLOSE Exit EndSwitch WEnd encrypt2exe.au3
-
I'm attempting to decrypt a file previously encrypted with the encrypt file function; then read that file into an array and display it. When I read the file into an array it still shows me garbled text if any at all. What am I doing wrong here? $serial = "stepping through array var" $FileHandle = "C:\XXX\Serial.txt" If FileExists($FileHandle) Then $Password = "password" _Crypt_DecryptFile($FileHandle, $FileHandle, $Password, $CALG_RC4) $FileArray = 0 ;initilze computer list array _FileReadToArray($FileHandle, $FileArray) _ArrayDisplay($FileArray) ;why is this showing encrpyted data?!?! FileOpen($FileHandle) FileWriteLine($FileHandle, $serial) FileClose($FileHandle) Else FileOpen($FileHandle) FileWriteLine($FileHandle, $serial) FileClose($FileHandle) EndIf $Password = "password" _Crypt_EncryptFile( $FileHandle, $FileHandle, $Password, $CALG_RC4) Next Any help is greatly appreciated!
- 4 replies
-
- encryption
- decryption
-
(and 2 more)
Tagged with: