-
Posts
1,585 -
Joined
-
Days Won
48
TheXman last won the day on February 22
TheXman had the most liked content!
Profile Information
-
Member Title
Semper volens adiuvare qui merentur
Recent Profile Visitors
10,622 profile views
TheXman's Achievements
-
 TheXman reacted to a post in a topic:
_StringToTable
TheXman reacted to a post in a topic:
_StringToTable
-
 argumentum reacted to a post in a topic:
JSON UDF using JSON-C
argumentum reacted to a post in a topic:
JSON UDF using JSON-C
-
Are your tests being run on virtual machines or physical machines?
-
 argumentum reacted to a post in a topic:
JSON UDF using JSON-C
argumentum reacted to a post in a topic:
JSON UDF using JSON-C
-
Your updated zip file includes jq code in the SpeedComparison.au3 script, but it does not include the required jq.udf and jq-win64.exe files.
-
 mLipok reacted to a post in a topic:
JSON UDF using JSON-C
mLipok reacted to a post in a topic:
JSON UDF using JSON-C
-
 Musashi reacted to a post in a topic:
JSON UDF using JSON-C
Musashi reacted to a post in a topic:
JSON UDF using JSON-C
-
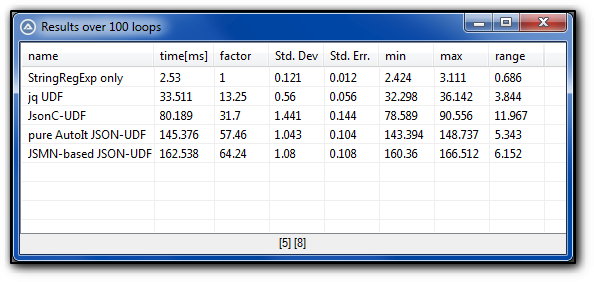
jq is very fast and it is very powerful too. It can do much more than parse JSON. jq is a JSON processor. Meaning, a lot of the post-processing of JSON data that you would normally do using AutoIt functions can be accomplished using jq, in a single jq filter, and be done much quicker too. The jq UDF has a few examples included in the zip file and jqPlayground has many more (20+) example jq filters to help you get started learning what jq can do. jqPlayground can be very helpful as a learning tool because it is interactive and allows you to save and restore sessions.
-
 TheXman reacted to a post in a topic:
JSON UDF using JSON-C
TheXman reacted to a post in a topic:
JSON UDF using JSON-C
-
 mLipok reacted to a post in a topic:
JSON UDF using JSON-C
mLipok reacted to a post in a topic:
JSON UDF using JSON-C
-
 AspirinJunkie reacted to a post in a topic:
JSON UDF using JSON-C
AspirinJunkie reacted to a post in a topic:
JSON UDF using JSON-C
-
Here are the results with jq added to the mix. This was run on a 10 year old Dell XPS 8700 running Windows 7 64bit. That explains the slower speeds overall.
-
 TheXman reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
TheXman reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
-
 SOLVE-SMART reacted to a post in a topic:
[Completed] Volunteers wanted 👀 to test an AutoIt + SQLite project
SOLVE-SMART reacted to a post in a topic:
[Completed] Volunteers wanted 👀 to test an AutoIt + SQLite project
-
 TheXman reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
TheXman reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
-
 TheXman reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
TheXman reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
-
 TheXman reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
TheXman reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
-

CryptoNG UDF - Cryptography API: Next Gen
TheXman replied to TheXman's topic in AutoIt Example Scripts
It appears that you want to store the public key blob in a variable or constant within you script and use it to encrypt data. If that's correct, then you can do that, but you will need to use a modified version of the internal __CryptoNG_BcryptImportKeyPair() function. Currently, that internal function reads in the public key blob from a specified file. All you would need to do is create a version of that function that reads the public key blob from your variable or constant instead. You would also need a slightly modified version of _CryptoNG_RSA_EncryptData() that passes that variable or constant to you modified version of __CryptoNG_BcryptImportKeyPair(). Another solution, which wouldn't require modifications to any of the existing CryptoNG functions, would be to embed the blob file in the script and have the script copy the file to the local file system using FileInstall(). Since it's a public key, you could leave it on the file system after your script exits. If you don't want to leave it, then you could just have the script delete it when you're finished with it. -
 Musashi reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
Musashi reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
-
 kroman82 reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
kroman82 reacted to a post in a topic:
CryptoNG UDF - Cryptography API: Next Gen
-

CryptoNG UDF - Cryptography API: Next Gen
TheXman replied to TheXman's topic in AutoIt Example Scripts
Ah yes, you're right. I forgot about that. You cannot import a LEGACY_RSAPUBLIC_BLOB using BCryptImportKeyPair. However, you can import a LEGACY_RSAPRIVATE_BLOB (if it is available). And from that LEGACY_RSAPRIVATE_BLOB, you can export an RSA public key blob and/or an RSA private key blob. The conversion of just a legacy public key blob or PEM to an RSA public key blob would be a little more difficult...but still doable. I'll put that on my list of feature requests for CryptoNG. -
 kroman82 reacted to a file:
CryptoNG UDF - Cryptography API: Next Generation
kroman82 reacted to a file:
CryptoNG UDF - Cryptography API: Next Generation
-

CryptoNG UDF - Cryptography API: Next Gen
TheXman replied to TheXman's topic in AutoIt Example Scripts
You're welcome! Creating such a function wouldn't be very difficult at all. Actually, the API wrappers/functions to read in a legacy private key blob file and create either (or both) the rsa public and private key blob files already exist in the UDF library. Or, as you suggested, the same could be done with just the public key blob file. I could post such a function but where's the fun in that for others that may want to try to do it themselves? OpenSSL already has the ability to convert PEM's to legacy blob files. So those blob files could be used as input to a CryptoNG function that converts them to rsa blob files. Hint: https://learn.microsoft.com/en-us/windows/win32/api/bcrypt/nf-bcrypt-bcryptimportkeypair https://learn.microsoft.com/en-us/windows/win32/api/bcrypt/nf-bcrypt-bcryptexportkey -

CryptoNG UDF - Cryptography API: Next Gen
TheXman replied to TheXman's topic in AutoIt Example Scripts
@kroman82 I have uploaded a new version of CryptoNG. The new version includes a function (_CryptoNG_RSA_CreateKeyPairEx) that will export both types of blob files (RSA and MS/Legacy). The RSA blob files are needed by Microsoft's CryptoNG API's (which are what my UDF creates wrappers for). The MS blob files can be used to generate PEM or DER files that can be used with OpenSSL or any other crypto library that has RSA functions. Here is an updated CryptoNG example that uses the new function: Func rsa_public_private_key_encrypt_decrypt_data_example() Const $ALG_ID = $CNG_BCRYPT_RSA_ALGORITHM, _ $MESSAGE = "This is a super-secret message.", _ $RSA_PUBLIC_KEY_FILE = "rsa_publickey.blob", _ $RSA_PRIVATE_KEY_FILE = "rsa_privatekey.blob", _ $MS_PUBLIC_KEY_FILE = "ms_publickey.blob", _ $MS_PRIVATE_KEY_FILE = "ms_privatekey.blob" Local $sDecryptedMessage = "" Local $xEncryptedMessage = Binary("") ;Create RSA Public/Private Key Pair _CryptoNG_RSA_CreateKeyPairEx(1024, $RSA_PUBLIC_KEY_FILE, $RSA_PRIVATE_KEY_FILE, $MS_PUBLIC_KEY_FILE, $MS_PRIVATE_KEY_FILE) If @error Then write_to_log("ERROR: " & _CryptoNG_LastErrorMessage() & @CRLF) Return False EndIf ;Encrypt plain text message $xEncryptedMessage = _CryptoNG_RSA_EncryptData($MESSAGE, $RSA_PUBLIC_KEY_FILE) If @error Then write_to_log("ERROR: " & _CryptoNG_LastErrorMessage() & @CRLF) Return False EndIf ;Decrypt encrypted message $sDecryptedMessage = _CryptoNG_RSA_DecryptData($xEncryptedMessage, $RSA_PRIVATE_KEY_FILE) If @error Then write_to_log("ERROR: " & _CryptoNG_LastErrorMessage() & @CRLF) Return False EndIf ;Display results write_to_log(@CRLF) write_to_log("CryptoNG Asymmetric Public/Private Key Encrypt/Decrypt Example" & @CRLF) write_to_log(StringFormat("%s Public key file = %s", $ALG_ID, $RSA_PUBLIC_KEY_FILE) & @CRLF) write_to_log(StringFormat("%s Private key file = %s", $ALG_ID, $RSA_PRIVATE_KEY_FILE) & @CRLF) write_to_log(StringFormat("%s Plain text message = %s", $ALG_ID, $MESSAGE) & @CRLF) write_to_log(StringFormat("%s Encrypted Message = %s", $ALG_ID, $xEncryptedMessage) & @CRLF) write_to_log(StringFormat("%s Decrypted Message = %s", $ALG_ID, $sDecryptedMessage) & @CRLF) EndFunc Result: CryptoNG UDF v2.3.0 CryptoNG Asymmetric Public/Private Key Encrypt/Decrypt Example RSA Public key file = rsa_publickey.blob RSA Private key file = rsa_privatekey.blob RSA Plain text message = This is a super-secret message. RSA Encrypted Message = 0x09240F7929B217338E10B94C6B481027C61B1C41080A806C02019A724B06991190BEFF5A27FBF17E0E6550067FAEAAB504936B2F4A55C0C2CC37F788B18C276CC31DCD339A5084FFF66A12E9598EF79432975EEE7A347F899AA38661B2FF3330418882F29A8B52012D8B57B85CF4DBD9924D7C606BE3A056FD66295B2D139B32 RSA Decrypted Message = This is a super-secret message. Done Upon successful execution of _CryptoNG_RSA_CreateKeyPairEx(), you should see the 4 blob files. To create PEM public/private key files for use by your server or other RSA crypto library functions, you can use OpenSSL to create PEM files like this. You can also create DER files by changing the -outform parameter. OpenSSL commands to convert MS KEYBLOB files to PEM files ---------------------------------------------------------- openssl rsa -pubin -inform "MS PUBLICKEYBLOB" -in ms_publickey.blob -outform PEM -out ms_publickey.pem openssl rsa -inform "MS PRIVATEKEYBLOB" -in ms_privatekey.blob -outform PEM -out ms_privatekey.pem -

CryptoNG UDF - Cryptography API: Next Gen
TheXman replied to TheXman's topic in AutoIt Example Scripts
I was going to reply earlier to clear up some of your confusion, but I decided to wait until I figured out a good solution. First, working with RSA keys IS very confusing, especially when you are working with CryptoNG (BCRYPT) RSA API's. Part of the reason is that CryptoNG RSA API's use RSA KEYBLOB files, not MS KEYBLOB files. MS KEYBLOB files are the blob files that were used with the deprecated CryptoAPI (ADVAPI32) API's and also the type that can be generated by OpenSSL. Unfortunately, OpenSSL does not have a way to create RSA KEYBLOB files -- at least not to my knowledge. You were trying to use MS KEYBLOB files with CryptoNG API's and that will not work. There are several other things that make working with RSA key pairs confusing, especially when you add in 3rd party tools like OpenSSL for key pair generation. As you have probably figured out, the CryptoNG UDF library function that creates RSA key pairs only exports them in one format or the other (RSA or Legacy). I am creating an extended function that will export both formats at once. Having both blob formats, you can use the RSA blob format for AutoIt CryptoNG functions to encrypt or decrrypt and use the legacy blob format (MS BLOBKEY) to convert the keys for use by other processes and libraries using the PEM or DER format. The OpenSSL conversion commands to convert legacy blob files to PEM or DER are in the CryptoNG Help File that is supplied with the UDF library. Give me about an hour to create the new function and test it. I will post it here when I'm done. -

CryptoNG UDF - Cryptography API: Next Gen
TheXman replied to TheXman's topic in AutoIt Example Scripts
If you used the parameters that you posted, why did you use my example private key with your newly generate public key? RSA uses public/private key pairs. If you want to test your newly generated keys using the provided example function, then you would need to use your newly generated public/private key pair as parameters. You can't mix & match RSA key pairs and expect that function to be able to encrypt and decrypt a message. If you want to be able to use externally created RSA key pairs (like the ones generated by openssl) with CryptoNG APIs, make sure that you read & understand the information in the "Remarks" section of the _CryptoNG_RSA_CreateKeyPair() entry in the CryptoNG help file. Microsoft's CryptoNG encryption/decryption functions can only import and use RSA-formatted keys. -
You're welcome.
-
The "%" in StringForma()t has to be escaped when you actually want a literal "%" character. You do it by using %% (like %%header{Dropbox-Api-Result}). If you would have used ConsoleWrite to view your command line, you would have seen that it did not produce your desired result.
-
If you are using curl and you are looking specifically for the value of the "Dropbox-Api-Result" response header, then I would add the -w / --write-output parameter to the command line to get that value. To get just that value, it would look something like -w %header{Dropbox-Api-Result}. If you want all of the headers in an easy to process JSON format, then I would use -w %{header_json} and use your favorite json udf to get the values of interest. The example below will return just the value of the date response header: curl -s -w %header{date} -o nul https://www.autoitscript.com curl -s -w "%header{date}" -o nul https://www.autoitscript.com
-
Instead of parsing the values of http response headers manually, why don't you use something that will retrieve individual header values for you like: winhttp api, winhttp com, or curl? What are you currently using to get the http response?