Search the Community
Showing results for tags '(Trojan.Win32.Agent.EDM)'.
-
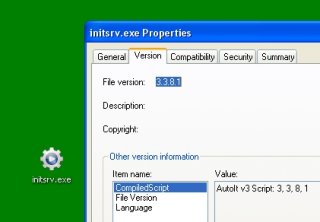
This morning, I'm off searching far and wide for a specific application... And I'm starting to jump into sites with Chinese and Arabic fonts, and sites with .pl and .ru suffixes. I'm know I'm tempting fate. I do have my "panic button" next to the clock that switches me to a basic startup profile (via msconfig), launches rkill.exe, and disables the internet. Half the time I'm able to clean the garbage off without a reboot. Some of the ransomware infects faster than my guards go up, but my default user account is not an administrator, and coming back in as Administrator has worked with all of the fake FBI crap. Worst case scenario, I just pull the drive and hang it off another PC as the D: drive and give it a cleaning. Anyway, I was loading some site, there's a freeze, then boom, Firefox windows start popping up like crazy. I killed the whole browser group, disabled my Local Area Connection and started looking around. Looking at running processes "winvnc86.exe" has red flags all over it as I've become very familiar with what belongs in the process list. I killed winvnc86 and things seeming safe enabled my connection, , started updating combofix and malwarebytes to their latest versions and then googled the winvnc86 filename. I clicked on the first few relevant sites to open in separate tabs and then my pc slowed, I got redirected, popups started again. I locked up and ran the cleaning programs. The popups were due to a couple executables stuck in my "user/local settings/temp" folder, and my 14KB svchost.exe had blossomed to 300KB. It's the other virus that caught my eye, a fairly new variant I guess. It's the one with the winvnc86.exe process, and it had downloaded 3 files to my system32 folder and was getting me setup to mine for bitcoin or litecoin. What I found interesting was that the driver/installer for it all, that had been parked in my "startup" folder, was a bound Autoit 3.3.8.1 executable, 571KB in size, called initsrv.exe. It's actions are well-described here: http://www.tgsoft.it/english/news_archivio_eng.asp?id=562 I found it a wierd mix of both shock and amusement that something malicious, with such an origin, would ever find it's way to my desktop.