Search the Community
Showing results for tags 'firewall'.
-
Hello 🙂 I'd like to have some hints how to handle Win firewall rules. Found this UDF for Win Vista.. Has someone experience with it? Will it work well for Win 10/11? Is there an example how to get (filtered) rules as array? Thanx a lot 🙂
-
I dug this UDF out in response to a request in the General Help forum. There is still some tidying to do, but I thought I would post here for anyone that would benefit. All functions have been tested on both XP and Windows 7. Updated January 22, 2014: Tested on XP, WIN7 and WIN8.1, x86 and x64 Current version includes: Enable or Disable the Windows Firewall Add or Remove Authorized Applications to the Exclusions list Add or Delete Ports from the Exclusions list. Enable or Disable the use of Exceptions Enable or Disable Notifications of blocked applications Enable or Disable Existing Ports List all Applications in the Exclusions List List all Ports in the Exclusions List List Properties of the current Firewall Configuration Restore the Windows Firewall to its default configuration Windows Firewall.au3
- 37 replies
-
- windows firewall
- udf
-
(and 1 more)
Tagged with:
-
Recently I was looking for a way to set DefaultInboundAction and DefaultOutboundAction for Windows firewall First I tried 'netsh.exe advfirewall set allprofiles firewallpolicy blockinbound,blockoutbound' However, it turns out group policy overrides these settings. I then went looking for a way to set the Firewall group policy and the best I could find was making a policy and copying it to the system32\grouppolicy folder and then running gpupdate.exe /force Instead of relying on such a rigid procedure I instead decided to parse the Registry.pol file and change the values within. This code has only been tested on W7x64 The example as supplied sets the domain profile firewall off the sets it back to the previous settings after you click the message box There are several options: Func SetGroupPolicy_Firewall($iSetting, $iValue, $sPath, $sProfile = "") Setting=0 Enable disable firewall , $iValue=0 Disable, $iValue=1 Enable Setting=1 DefaultInboundAction, $iValue=0 Allow, $iValue=1 Block Setting=2 DefaultOutboundAction, $iValue=0 Allow, $iValue=1 Block Profile ="" SET ALL PROFILES The profile can also be defined Profile= Domain;Private;Public Beware $iValue is only configured for 0 and 1 values there are a few more options on the inbound and outbound settings that I haven't given a way to set, so in this case you may need to copy back the registy.pol.bak file to revert to your previous settings It doesn't seem to have any issues on reverting back to original settings if Block all Exceptions or NotConfigured are set It just won't work which in my case is acceptable It wouldn't be too hard to add code to make these work as well: "[SOFTWARE\Policies\Microsoft\WindowsFirewall\DomainProfile" & CHRW(0) & ";DefaultInboundAction" & CHRW(0) & ";" & CHRW(4) & CHRW(0) & ";" & CHRW(4) & CHRW(0) & $iValue & CHRW(0) & "]" ;And Again for: ;[SOFTWARE\Policies\Microsoft\WindowsFirewall\DomainProfile;DoNotAllowExceptions;;;] Do note that these would need to be added for each profile. Domain;Public;Private. These locations do refer to actual registry locations but I haven't figured out a way to get those to change the group policy. If you run into problems or make improvements let me know a backup is saved as C:\Windows\System32\GroupPolicy\Machine\Registry.pol.bak just in case #RequireAdmin #include <WinAPIFiles.au3> Local $iLast If @OSArch = "X64" And @AutoItX64 = 0 Then $iLast = SetGroupPolicy_Firewall(0, 0, @WindowsDir & "\SysNative\GroupPolicy\Machine\Registry.pol", "Domain") Run(@ComSpec & " /c " & "gpupdate.exe /force", "", @SW_HIDE) Else $iLast = SetGroupPolicy_Firewall(0, 0, @WindowsDir & "\SysTem32\GroupPolicy\Machine\Registry.pol", "Domain") Run(@ComSpec & " /c " & "gpupdate.exe /force", "", @SW_HIDE) EndIf ConsoleWrite($iLast & ", ") MsgBox(0, "When Ready", "press Ok to go back to previous settings") If @OSArch = "X64" And @AutoItX64 = 0 Then $iLast = SetGroupPolicy_Firewall(0, $iLast, @WindowsDir & "\SysNative\GroupPolicy\Machine\Registry.pol", "Domain") Run(@ComSpec & " /c " & "gpupdate.exe /force", "", @SW_HIDE) Else $iLast = SetGroupPolicy_Firewall(0, $iLast, @WindowsDir & "\SysTem32\GroupPolicy\Machine\Registry.pol", "Domain") Run(@ComSpec & " /c " & "gpupdate.exe /force", "", @SW_HIDE) EndIf ConsoleWrite($iLast & @CRLF) Func SetGroupPolicy_Firewall($iSetting, $iValue, $sPath, $sProfile = "") Local $sCommand, $sSearch, $sFile Local $hFile Local $iFileEnd, $iLenSearch, $iFound = 0, $iError = 0, $iReturn = -1 If $iValue >1 or $iValue<0 Then $iSetting=-1 Switch $iSetting Case 0 $sCommand = ";EnableFirewall" Case 1 $sCommand = ";DefaultInboundAction" Case 2 $sCommand = ";DefaultOutboundAction" Case Else ConsoleWrite("SetGroupPolicy_Firewall Invalid Command " & $iSetting) $iError = 1 EndSwitch If $sProfile <> "" Then $sProfile = "\" & StringMid(StringUpper($sProfile), 1, 1) & StringMid(StringLower($sProfile), 2, -1) $sSearch = $sProfile & "Profile" & ChrW(0) & $sCommand FileSetAttrib($sPath, "-RH") ;Remove readonly and hidden attributes these mess up windows policy editor FileCopy($sPath, $sPath & ".Bak", 0) ;Make a backup of policy file if one doesn't exist $hFile = FileOpen($sPath, 0 + 16 + 32) ;read, Binary,UTF16_LE If $hFile = -1 Then ConsoleWrite("Error Opening" & @CRLF & $sPath & "> Exists=" & _WinAPI_FileExists($sPath)) $iError = 2 Else FileSetPos($hFile, 0, 2) ;EoF $iFileEnd = FileGetPos($hFile) FileSetPos($hFile, 0, 0) ;Beginning $sSearch = StringToBinary($sSearch, 2) $iLenSearch = BinaryLen($sSearch) If $iLenSearch > 32 Then $sFile = BinaryToString(FileRead($hFile, -1)) For $i = 0 To $iFileEnd Step 2 FileSetPos($hFile, $i, 0) ;Beginning If FileRead($hFile, $iLenSearch) = $sSearch Then $iFound += 1 FileSetPos($hFile, $i + $iLenSearch + 16, 0) $iReturn = Int(Hex(BinaryMid(StringToBinary($sFile), $i + $iLenSearch + 16, 2))) $sFile = StringMid($sFile, 1, $i + $iLenSearch + 16) & ChrW($iValue) & StringMid($sFile, $i + $iLenSearch + 16 + 2, -1) EndIf Next FileClose($hFile) If $iFound > 0 Then $hFile = FileOpen($sPath, 2 + 16 + 32) ;Overwrite,Binary,UTF16_LE If Not (FileWrite($hFile, $sFile)) Then ConsoleWrite("Unable to write to policy file" & @CRLF & $sPath & @CRLF) $iError = 4 $iReturn = -1 EndIf FileClose($hFile) Else ConsoleWrite("Search String Not Found" & @CRLF) $iError = 3 EndIf Else ConsoleWrite("Invalid Search String" & @CRLF) $iError = 5 EndIf ;FileSetAttrib($sPath, "+H") EndIf Return SetError($iError, $iFileEnd, $iReturn) EndFunc ;==>SetGroupPolicy_Firewall
- 1 reply
-
- firewall
- defaultinboundaction
- (and 3 more)
-
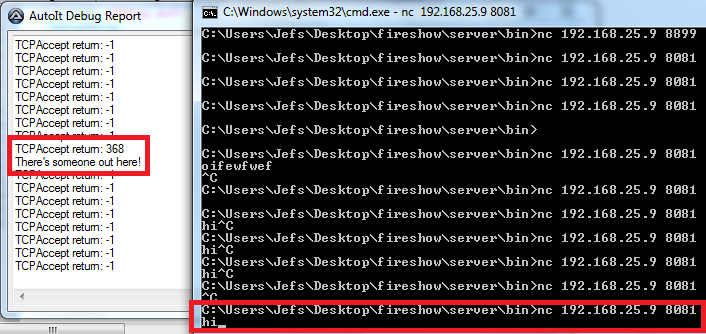
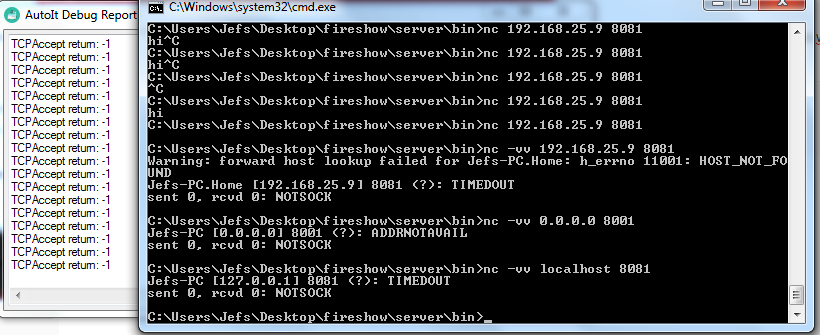
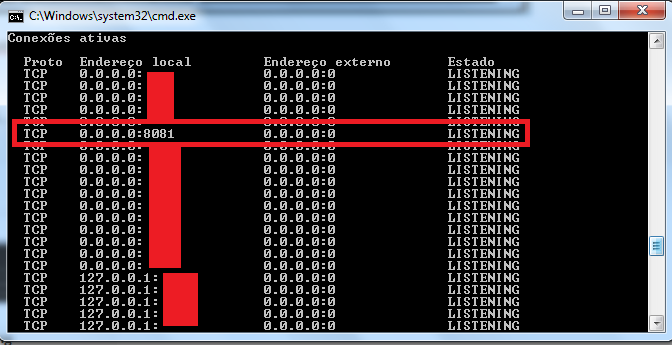
Hi guys! I'm having a trouble with TCPAccept() on compiled scripts. This script I made to test: #include <Debug.au3> _DebugSetup() TCPStartup() $Main = TCPListen("0.0.0.0", 8081) _DebugOut("TCPListen output: " & $Main) While True $ac = TCPAccept($Main) _DebugOut("TCPAccept return: " & $ac) If $ac <> -1 Then _DebugOut("There's someone out here!") TCPSend($ac, "hi") EndIf WEndWorks fine if I run it by pressing F5 on SciTe window. But if I compile it and then execute the executable file, it does not work. Instead, NetCat tells me that the connection timed out (I've tested other clients as well): I've checked if the port is really opened, if I really can open it, if there is other software using that port, but everything showed that it should connect. Btw, netstat -an shows that the port is really listening (when I execute my file). It listens, but does not accept. I use no antivirus software (I use this Windows installation for coding only) and Windows Firewall is disabled. I've tried, anyway, allowing my exe file on Firewall rules, but it also did not work. Running as administrator also did not help. I believe it's a Windows (Firewall?) bug rather than an AutoIt bug. How can I manage to solve this? Thanks in advance.
-
Hello, I'm trying to install AutoIT on a [Windows 2003] machine that has restricted access - I can't install any files, nor can I request or access Administrator rights. So far I've tried installing AutoIT on another machine (into a folder called AutoIt-Transfer), zipping that file, and unzipping it on the Windows 2003 virtual machine. It does work, however it doesn't work well. There are many restrictions - MsgBox does not work for example. Does anyone know of a workaround? For example, does AutoIT install files to the Windows directory? Maybe I can just copy/paste them in there? Thanks.
- 2 replies
-
- installing
- firewall
-
(and 1 more)
Tagged with: