About This File
Let's say you have some files you dont want anyone to know what they are,
and you dont want anyone to be able to open them, you could encrypt them,
but if the files are big it'll take a long time to do the operations for you to be able to open those files.
I made this to make this process faster, and still not easy for someone to open the files, or even know what type they are.
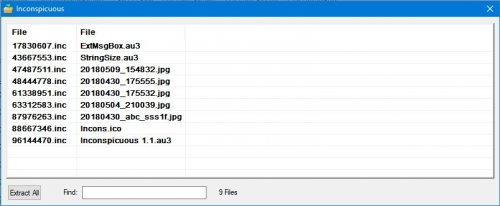
What it does is change the filename to a random number with 8 digits and .inc extension.
The original filename is encrypted in the file itself, with a PIN provided by the user up to 4 digits, this PIN is also a number that's going to be used to split the file and change it internally, so the end result is a file with a header that's got the original filename encrypted, and the rest of the file scrambled a bit.
The way it works is simple, place the application in a folder where you want to hide the files, it will ask for a pin, after you press ok, the application asks :
Encrypt or decrypt?
If encrypt, the files will become the 8 digit .inc files.
The originals will stay, the user can delete the originals or do whatever.
Then to open the files back, same process, but this time choose decrypt, and a listview will show the random filenames and the corresponding decrypted/original filenames and extension, uppon double click they open with whatever application is the default for them. There's a search feature, and an "extract all" button, to get all files back to original/unencrypted versions.
Feedback is wellcome.