Search the Community
Showing results for tags 'UAC'.
-
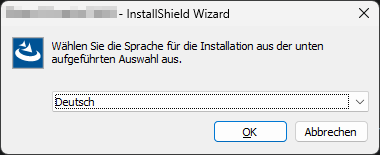
Hello all, I am aware that most of you may have seen similar questions being asked a lot. I've spent some days know to go through many of the propesed answers but so far none of those answers were able to help me to resolve the issue, i.e. interacting with a standard ComboBox of a third party software. I am doing this on Windows 11 (22H2) using AutoIt v3.3.16.1. What I am trying to do is to select a language from a ComboBox when running an InstallShield setup launcher (setup.exe). The only thing I managed so far is to read out the currently selected value that is being displayed: Local Const $sWndTitle = "InstallShield Wizard" Local Const $sCtrlClass = "[CLASS:ComboBox; INSTANCE:1]" WinActivate($sWndTitle) Local $hWnd = WinWaitActive($sWndTitle, "", 5) Local $sCurrentLang = ControlGetText($hWnd, "", $sCtrlClass) ConsoleWrite("$sCurrentLang: " & $sCurrentLang & @CRLF) ; OK Considering this dialog this gives me "$sCurrentLang: Deutsch" on the console. So far, so good. Now the issue is that I can't figure out how to select a different value from that ComboBox. I've tried all kinds of things ranging from all sorts of Control Name variations to different methods I found here in this forum, on StackOverflow, the web, like: ControlSetText($hWnd, "", "[CLASS:ComboBox; INSTANCE:1]", "Englisch", 1) ControlSend($hWnd, "", "[CLASS:ComboBox; INSTANCE:1]", "E") ControlSend($hWnd, "", "[CLASS:ComboBox; INSTANCE:1]", "Englisch") ControlCommand($hWnd, "" , "[CLASS:ComboBox; INSTANCE:1]" , "SelectString" , "Englisch") ControlSend($hWnd, "", $hCtrl, "Englisch") _GUICtrlComboBox_SetCurSel(306, 1) ;ID from AutoIt Info Tool _GUICtrlComboBox_SetCurSel("ComboBox1", 1) ;... The AutoIt Info Tool gives the following information about the ComboBox: >>>> Window <<<< Title: ABC - InstallShield Wizard Class: #32770 Position: 1088, 617 Size: 384, 157 Style: 0x94C808C4 ExStyle: 0x00010101 Handle: 0x00000000000D0910 >>>> Control <<<< Class: ComboBox Instance: 1 ClassnameNN: ComboBox1 Name: Advanced (Class): [CLASS:ComboBox; INSTANCE:1] ID: 306 Text: Position: 51, 65 Size: 317, 21 ControlClick Coords: 120, 19 Style: 0x50010343 ExStyle: 0x00000004 Handle: 0x00000000003F10EC I also tried other CombBox related functions, for example: ControlCommand("InstallShield", "", "ComboBox1","ShowDropDown", "") but nothing worked, except ControlGetText(). I would be very thankful if anybody could give me a hint on how to interact with this ComboBox. If anything is unclear or missing please do not hesitate to ask. Best regards, Tacomas Edit: This might be a Windows 11 issue, since I just found that I also can't click a button on this dialog. Either this or I completely misunderstood how to use AutoIt to interact with UI controls. WinActivate($sWndTitle) If ControlClick($sWndTitle, "", "[CLASS:Button; INSTANCE:2]") = 0 Then ConsoleError("ERROR: ControlClick() failed!" & @CRLF) ;no click, no error
-
Hi! I have a program that has a specific function that renames the computer. The entire program should be executed only on behalf of the current user, because some registry keys in the HKCU are being changed. The current user does not have administrator rights, so #Requireadmin is not suitable as a solution. The administrator accounts on the computers are different, so "RunAs" is not suitable. Is there a way to trigger a UAC, when running a function? The function code, if you need: Func _RenamePC($Input2) Local $Name = GUICtrlRead($Input2) $objWMIService = ObjGet("winmgmts:\root\cimv2") For $objComputer In $objWMIService.InstancesOf("Win32_ComputerSystem") $oReturn = $objComputer.rename($Name) Next EndFunc
-
Hi there! 😃 I've 2 simple scripts: Script 1 starts script 2 Script 1 gets executed with normal user rights (un-elevated) Script 2 contains an #RequireAdmin and therefor can only start elevated I want to read the output of script 2 with script 1 AND have the UAC of script 2 being activated as fullscreen Script 1 (Scripts location is the same as script 2 that I'm running with Run() Local $iPID, $sOutput $iPID = Run(@ComSpec & " /c " & "C:\Entwicklung\Autoit\Test\Temp.exe", @ScriptDir, @SW_HIDE, 0x2) ProcessWaitClose($iPID) $sOutput = StdoutRead($iPID) StdioClose($iPID) ConsoleWrite($sOutput) MsgBox(1, 1, 1) Script 2 (compiled as Temp.exe) #RequireAdmin ConsoleWrite("Return") MsgBox(1,1,"ADMIN") Now my problems are the following: Without the #RequireAdmin I can read the output with no problem, but not with the #RequireAdmin ($sOutput is empty) Using @SW_HIDE in the Run() command makes the UAC always start minimized (see attached picture) and the admin has to always manually click on the icon to enter his credentials since the UAC doesn't start in fullscreen. Here and on a few other sites they explain that the program launching the elevated program NEEDS to be activated in order to directly show the UAC fullscreen and not minimized. Using @SW_SHOW would get rid of the problem, BUT that leaves me with an ugly cmd.exe floating the whole time while the elevated script ist running. And my questions to that I'm seeking an answer for are: Problem 1: Is it just not possible to read from an elevated program with an un-elevated user/script? I also get the Access Denied if I press No on the UAC as an Output in $sOutput (Guess since its's still un-elevated) Problem 2: Is there a way to either make the floating black and blank cmd.exe being moved to the background and be non visible to the user OR to somehow bring the minimized UAC to the foreground/fullscreen? What I already tried and what didn't help me: $iPID = Run(@ComSpec & " /c " & "C:\Entwicklung\Autoit\Test\Temp.exe", @ScriptDir, @SW_HIDE, 0x2) While Not WinExists("Temp.exe erfordert Ihre Berechtigung") ConsoleWrite(1) WEnd WinActivate("Temp.exe erfordert Ihre Berechtigung") WinSetState("Temp.exe erfordert Ihre Berechtigung", WinGetText("Temp.exe erfordert Ihre Berechtigung"), @SW_SHOW) WinSetState("Temp.exe erfordert Ihre Berechtigung", WinGetText("Temp.exe erfordert Ihre Berechtigung"), @SW_MAXIMIZE) WinSetState("Temp.exe erfordert Ihre Berechtigung", WinGetText("Temp.exe erfordert Ihre Berechtigung"), @SW_ENABLE) The While-Loops helps a lot and also stops after a second or so (► Stops to write ones (1)). That means that the actual "window" of the UAC is found, but all the WinXXX functions don't do anything and the UAC stays minimized. I also tried to minimized/move the cmd.exe to the background with WinActivate() and WinSetState() with no success. $iPID = ShellExecute("C:\Entwicklung\Autoit\Test\Temp.exe", "", @ScriptDir, "open", @SW_HIDE) Using ShellExecute() instead of Run() completely solves the UAC to fullscreen problem BUT I haven't found a consistent way to read the output of ShellExecute(). Neither here on the forum nor somewhere else. If I'd be possible to read the output from ShellExecute() then all my problems would be solved at once! Also tried a few more things and playing with some parameters but everything with no success. I'd really love some help and support here from you. Thanks in advance!
-
Hi, When a non compiled AU3 script is run with #RequireAdmin, then if the UAC prompt can be authorized due to the fact, that the currently loggedon user has local admin rights, then the macro @UserProfileDir correctly reflects the profile dir of the user of the windows logon session. When the script with #RequireAdmin is started by a "normal user" without local admin rights, and I use a domain admin account to authorize the UAC prompt, then @UserProfileDir reflects the profile dir belonging to the AD-Admin account. As the script originally was started using the "regular user" I'm wondering, if there is a chance to "pass" the original user's @UserProfileDir to the UAC elevated script? As playing around with this feature I realize, that I basically don't know the exact mechanism of the UAC elevation authorization process: The script is started by right mouse click, execute script This is invoking e.g. "C:\Program Files (x86)\AutoIt3\AutoIt3.exe" "C:\Users\Rudi\Desktop\test.au3" as by this registy value: Windows Registry Editor Version 5.00 [HKEY_CLASSES_ROOT\AutoIt3Script\Shell\Run\Command] @="\"C:\\Program Files (x86)\\AutoIt3\\AutoIt3.exe\" \"%1\" %*" But what I honestly don't know is, how does the UAC propt interact in the program startup? I guess, that Autoit3.exe is parsing the AU3 source, is seeing the #RequireAdmin and then "relaunches itself with the AU3 as %1" requesting UAC elevated rights "from windows"??? With Process Explorer I can see, that The commandline then is this one with a "!" before "%1" "C:\Program Files (x86)\AutoIt3\AutoIt3.exe" !"C:\Users\Rudi\Desktop\test.au3" It it should be something like this, then it might be possible to pass the original @UserProfileDir to the second, UAC elevated "Startup"??? <edit> I just noticed: When I use "WIN+R" and then directly use the command line, I see in Process Explorer, ... "C:\Program Files (x86)\AutoIt3\AutoIt3.exe" !"C:\Users\Rudi\Desktop\test.au3" ... then this script with #RequireAdmin is started *WITHOUT* UAC elevation. Guessing, that this ! is just reverting #RequireAdmin I tried the "opposite" one as well: AU3 script without #RequireAdmin Starting with "C:\Program Files (x86)\AutoIt3\AutoIt3.exe" !"C:\Users\Rudi\Desktop\test.au3" does not invoke UAC elevation prompt. So to me it looks like, this ! is a "status flag from Autoit3.exe to Autoit3.exe", that the elevation process was done already? amazing... the topic Autoit on Windows Vista is telling no details of this UAC process... </edit> Regards, Rudi.
- 7 replies
-
- uac
- requireadmin
-
(and 1 more)
Tagged with:
-
Hi everyone, i am writing to you after a very long struggle i had while trying to figure out how to send a simple click inside a virtual machine running in vmware workstation 14. i have an autoit script running on my host machine watching for the UAC prompt to be displayed in a running vm. Both the host and the guest OS are Windows 10. This script worked perfectly with virtual box. It recognized the UAC prompt and clicked inside and the UAC was accepted. Since i switched to VMware Workstation 14, the script no longer clicks inside the VM successfully. It acts as if it clicks, but it doesn't. I tried sending key combinations instead of a click, so that the VM can grab the input, but it also did not work. Every attempt that i made to send clicks or keys from the host inside the VM did not work. I tried using: MouseClick ControlClick MouseMove _WinAPI_Mouse_Event _WinAPI_Keybd_Event I also noticed that while the cursor moves to the target which has to be cilcked when my vmware worstation window is not focused, it even doesn't do that when i WinActivate the vmware workstation window first. Did anyone experience such an issue, or maybe could give me a hint, what else i could use to send a key combination or a mouse click in a vmware workstation 14 pro guest window? here is my code, which works with virtualbox: #AutoIt3Wrapper_Icon=".\uac.ico" #include <ImageSearchSubrogated.au3> FileInstall(".\ImageSearchDLL.dll", ".\ImageSearchDLL.dll", 0) FileInstall(".\UAC_ginloSetup.bmp", ".\UAC_ginloSetup.bmp", 0) FileInstall(".\UAC_Yes.bmp", ".\UAC_Yes.bmp", 0) ; set global variables for the coordinates, which should be delivered global $x1 = 0, $y1 = 0 global $x2 = 0, $y2 = 0 global $counter1 = 0 global $counter2 = 0 global $sleep = 10000 global $smallSleep = 5000 ; execute the script in a loop, so that it will hopefully recover from some unexpected errors While $counter1 < 1 checkForImage() WEnd #cs ------------ Functions #ce ------------ Func checkForImage() While $counter2 < 1 ; search for the UAC in the entire screen - 2 screens supported local $searchUac = _ImageSearchArea('UAC_ginloSetup.bmp', 1, -2568, -8, 5136, 1440, $x1, $y1, 0) If $searchUac = 1 Then ; if the UAC was found search for the Yes button in a an area 200 x 200 from the middle of the found UAC image local $searchYes = _ImageSearchArea('UAC_Yes.bmp', 1, $x1, $y1, $x1 + 200, $y1 + 200, $x2, $y2, 0) If $searchYes = 1 Then ; if the Yes button was found click it and pause the script for $sleep seconds MouseClick("left", $x2, $y2, 1,0) Sleep($sleep) Else ; if the Yes button was not found retry from the beginning in $smallSleep seconds MsgBox(0, "UAC found error", "UAC was found but the 'Yes' button was not found. Script will retry in " & $smallSleep & " seconds.", $smallSleep) EndIf ; another way to accept the UAC - via shortcut ;Send("{TAB}{TAB}{TAB}{TAB}{TAB}{TAB}") ;Send("!y") Else ; if UAC was not found try again in $sleep seconds Sleep($sleep) EndIf WEnd ; if some error occured which expired the loop, pause the script for $sleep seconds MsgBox(0, "Error", "Some Error expired the timer and the script could not recover. The script will restart in " & $sleep & " seconds.", $sleep) EndFunc
-
Here's a short UDF that will, at least in most cases, detect whether a window can be copied from or pasted to programmatically--for example, by Send()ing ctl-c, ctl-v. This is often disabled when programs (like your AutoIt script) run at a lower UAC integrity level than the application they are trying to operate on. #include <WinAPI.au3> Func _WindowIsPasteable($handle) ;accepts window handle; returns true or false whether a window will accept Ctl-C, Ctl-V Local $bCanPaste = True Local $hTestWindowPID = 0 Local $hTestWindowTID = _WinAPI_GetWindowThreadProcessId($handle, $hTestWindowPID) _WinAPI_AttachThreadInput(_WinAPI_GetCurrentThreadId(), $hTestWindowTID, True);attach to window we want to paste into $bCanPaste = _WinAPI_GetFocus() ;Test whether window is paste-able--returns False if it is not _WinAPI_AttachThreadInput(_WinAPI_GetCurrentThreadId, $hTestWindowTID, False);detach from window thread Return $bCanPaste EndFunc Pass it a window handle; it returns true or false whether a window will accept programmatic pasting. The function may not work on the CMD window, since it handles the clipboard uniquely. This function works by attaching to the program thread of the window whose handle it receives, then attempting to perform a GetFocus on that thread. In most cases, the attempt will fail if the window will not accept programmatic copy-paste.
-
When I use the following code I receive an UAC message: #RequireAdmin RunWait("msiexec /i winzip205-64.msi /quiet") Exit How can I hide (bypass) the UAC message?
-
I'm writing a set of PowerShell scripts/library for Windows 10 builds. One thing I often want to do is to browse to the location of a script that is part of a larger group of scripts and run it manually to do an install or make a one off change. So I like all my scripts to work well whether run from a task sequence or double-clicked in explorer. Most of my build scripts rely on having admin rights so I like to make them able to self-elevate if required - or at least give an error message. In PowerShell 4.0 (Windows 8.1) they added the #Requires -RunAsAdministrator statement but this won't do it for you - it just causes the script to abort if not admin. Below is a PowerShell script that does the following: Checks for admin rights using the Test-IsAdmin functionIf not admin:Get the full script path and working directory using the Get-UNCFromPath functionIf the paths are mapped drives then get the UNC version (drive mappings are lost when elevating from user to admin in most configurations)Execute PowerShell.exe with the UNC path of the script and the RunAs verb to trigger elevation. ExecutionPolicy is also set to Bypass on the command line. The working directory is also set to the UNC path version.Waits for the new process to finish, and captures its return codeExits using the same return codeScript is as follows: # Test if admin function Test-IsAdmin() { # Get the current ID and its security principal $windowsID = [System.Security.Principal.WindowsIdentity]::GetCurrent() $windowsPrincipal = new-object System.Security.Principal.WindowsPrincipal($windowsID) # Get the Admin role security principal $adminRole=[System.Security.Principal.WindowsBuiltInRole]::Administrator # Are we an admin role? if ($windowsPrincipal.IsInRole($adminRole)) { $true } else { $false } } # Get UNC path from mapped drive function Get-UNCFromPath { Param( [Parameter(Position=0, Mandatory=$true, ValueFromPipeline=$true)] [String] $Path) if ($Path.Contains([io.path]::VolumeSeparatorChar)) { $psdrive = Get-PSDrive -Name $Path.Substring(0, 1) -PSProvider 'FileSystem' # Is it a mapped drive? if ($psdrive.DisplayRoot) { $Path = $Path.Replace($psdrive.Name + [io.path]::VolumeSeparatorChar, $psdrive.DisplayRoot) } } return $Path } # Relaunch the script if not admin function Invoke-RequireAdmin { Param( [Parameter(Position=0, Mandatory=$true, ValueFromPipeline=$true)] [System.Management.Automation.InvocationInfo] $MyInvocation) if (-not (Test-IsAdmin)) { # Get the script path $scriptPath = $MyInvocation.MyCommand.Path $scriptPath = Get-UNCFromPath -Path $scriptPath # Need to quote the paths in case of spaces $scriptPath = '"' + $scriptPath + '"' # Build base arguments for powershell.exe [string[]]$argList = @('-NoLogo -NoProfile', '-ExecutionPolicy Bypass', '-File', $scriptPath) # Add $argList += $MyInvocation.BoundParameters.GetEnumerator() | Foreach {"-$($_.Key)", "$($_.Value)"} $argList += $MyInvocation.UnboundArguments try { $process = Start-Process PowerShell.exe -PassThru -Verb Runas -Wait -WorkingDirectory $pwd -ArgumentList $argList exit $process.ExitCode } catch {} # Generic failure code exit 1 } } # Relaunch if not admin Invoke-RequireAdmin $script:MyInvocation # Running as admin if here $wshell = New-Object -ComObject Wscript.Shell $wshell.Popup("Script is running as admin", 0, "Done", 0x1) | Out-Null
- 5 replies
-
- powershell
- uac
-
(and 1 more)
Tagged with:
-
#RequireAdmin #include <WinAPISys.au3> #include <WindowsConstants.au3> _WinAPI_ChangeWindowMessageFilterEx ( $hWnd, $iMsg, $iAction ) ;_WinAPI_ChangeWindowMessageFilterEx( $hWnd, $WM_DROPFILES, $MSGFLT_ALLOW) ;_WinAPI_ChangeWindowMessageFilterEx( $hWnd, $WM_COPYDATA, $MSGFLT_ALLOW) ;_WinAPI_ChangeWindowMessageFilterEx( $hWnd, $WM_COPYGLOBALDATA, $MSGFLT_ALLOW) ; $WM_COPYDATA = 0x004A - $WM_DROPFILES = 0x0233 - $WM_COPYGLOBALDATA = 0x0049 - $MSGFLT_ALLOW = 1 - $MSGFLT_DISALLOW = 2Example: #RequireAdmin Opt("TrayAutoPause", 0) #include <WinAPISys.au3> #include <WindowsConstants.au3> #include <GUIConstantsEx.au3> #include <StaticConstants.au3> #include <ButtonConstants.au3> Global $AppWindows = GUICreate("Dao Van Trong - Trong.CF", 320, 50, -1, -1, BitOR($WS_BORDER, $WS_POPUP), BitOR($WS_EX_ACCEPTFILES, $WS_EX_TOPMOST, $WS_EX_WINDOWEDGE)) Global $AppTitle = GUICtrlCreateLabel("=== Drag and drop UAC ===", 56, 0, 210, 25, $SS_CENTERIMAGE, $GUI_WS_EX_PARENTDRAG) GUICtrlSetState(-1, $GUI_DROPACCEPTED) GUICtrlSetBkColor(-1, $GUI_BKCOLOR_TRANSPARENT) GUICtrlSetFont(-1, 9, 800) Global $AppTask = GUICtrlCreateLabel("Drag and drop files here ", 56, 24, 220, 17, $SS_CENTERIMAGE, $GUI_WS_EX_PARENTDRAG) GUICtrlSetState(-1, $GUI_DROPACCEPTED) GUICtrlSetBkColor(-1, $GUI_BKCOLOR_TRANSPARENT) GUICtrlSetFont(-1, 9, 500) Global $xCLOSE = GUICtrlCreateButton("X", 308, 0, 12, 12, BitAND($BS_MULTILINE, $BS_VCENTER, $BS_FLAT)) GUICtrlSetBkColor(-1, $GUI_BKCOLOR_TRANSPARENT) GUICtrlSetState(-1, $GUI_DROPACCEPTED) GUISetState(@SW_SHOW) _WinAPI_ChangeWindowMessageFilterEx($AppWindows, $WM_DROPFILES, $MSGFLT_ALLOW) _WinAPI_ChangeWindowMessageFilterEx($AppWindows, $WM_COPYDATA, $MSGFLT_ALLOW) _WinAPI_ChangeWindowMessageFilterEx($AppWindows, $WM_COPYGLOBALDATA, $MSGFLT_ALLOW) Global $__aDropFiles GUIRegisterMsg($WM_DROPFILES, "WM_DROPFILES") Local $nMsg While 1 $nMsg = GUIGetMsg() Switch $nMsg Case $GUI_EVENT_DROPPED If $__aDropFiles[0] > 0 Then For $i = 1 To $__aDropFiles[0] ConsoleWrite($__aDropFiles[$i] & @CRLF) GUICtrlSetData($AppTask, $__aDropFiles[$i]) Next EndIf Case $GUI_EVENT_CLOSE, $xCLOSE Exit EndSwitch WEnd Func WM_DROPFILES($hWnd, $iMsg, $iwParam, $ilParam) #forceref $hWnd, $ilParam Switch $iMsg Case $WM_DROPFILES Local $aReturn = _WinAPI_DragQueryFileEx($iwParam) If IsArray($aReturn) Then $__aDropFiles = $aReturn Else Local $aError[1] = [0] $__aDropFiles = $aError EndIf EndSwitch Return $GUI_RUNDEFMSG EndFunc ;==>WM_DROPFILES
- 6 replies
-
- drag and drop
- uac
-
(and 1 more)
Tagged with:
-
I found a few related topics for some reference: Basically the issue has always been how to interpret and work with the results of IsAdmin() when running under UAC, and the desire for developers to not force the use of #RequireAdmin (or the AutoIt3Wrapper manifest equivalent) for all of their users. A lot of programs have that nice 'Elevate' button which is presented to you when the function is available, to selectively elevate the application and enable administrative functions. Here's my attempt at detecting this scenario. The function will return the current admin status, and the ability of the current app to elevate itself under UAC in @extended. A small example should show how it is used. The example can be run from SciTE or compiled, allowing you to test all kinds of scenarios. Something interesting I found... if an app is launched from another fully elevated app, and that new app is launched with restricted privileges by way of the SAFER api, then that app CANNOT re-elevate itself to full admin status. The other way to lower a launched app's privileges uses either CreateProcessAsUser or CreateProcessWithTokenW (there are scripts on the forum that show their usage). Apps launched with either of those functions CAN re-elevate themselves to full admin status. _IsUACAdmin #include <Security.au3> ; #FUNCTION# ==================================================================================================================== ; Name ..........: _IsUACAdmin ; Description ...: Determines if process has Admin privileges and whether running under UAC. ; Syntax ........: _IsUACAdmin() ; Parameters ....: None ; Return values .: Success - 1 - User has full Admin rights (Elevated Admin w/ UAC) ; Failure - 0 - User is not an Admin, sets @extended: ; | 0 - User cannot elevate ; | 1 - User can elevate ; Author ........: Erik Pilsits ; Modified ......: ; Remarks .......: THE GOOD STUFF: returns 0 w/ @extended = 1 > UAC Protected Admin ; Related .......: ; Link ..........: ; Example .......: No ; =============================================================================================================================== Func _IsUACAdmin() ; check elevation If StringRegExp(@OSVersion, "_(XP|20(0|3))") Or (Not _IsUACEnabled()) Then ; XP, XPe, 2000, 2003 > no UAC ; no UAC available or turned off If IsAdmin() Then Return SetExtended(0, 1) Else Return SetExtended(0, 0) EndIf Else ; check UAC elevation ; ; get process token groups information Local $hToken = _Security__OpenProcessToken(_WinAPI_GetCurrentProcess(), $TOKEN_QUERY) Local $tTI = _Security__GetTokenInformation($hToken, $TOKENGROUPS) _WinAPI_CloseHandle($hToken) ; Local $pTI = DllStructGetPtr($tTI) Local $cbSIDATTR = DllStructGetSize(DllStructCreate("ptr;dword")) Local $count = DllStructGetData(DllStructCreate("dword", $pTI), 1) Local $pGROUP1 = DllStructGetPtr(DllStructCreate("dword;STRUCT;ptr;dword;ENDSTRUCT", $pTI), 2) Local $tGROUP, $sGROUP = "" ; ; S-1-5-32-544 > BUILTINAdministrators > $SID_ADMINISTRATORS ; S-1-16-8192 > Mandatory LabelMedium Mandatory Level (Protected Admin) > $SID_MEDIUM_MANDATORY_LEVEL ; S-1-16-12288 > Mandatory LabelHigh Mandatory Level (Elevated Admin) > $SID_HIGH_MANDATORY_LEVEL ; SE_GROUP_USE_FOR_DENY_ONLY = 0x10 ; ; check SIDs Local $inAdminGrp = False, $denyAdmin = False, $elevatedAdmin = False, $sSID For $i = 0 To $count - 1 $tGROUP = DllStructCreate("ptr;dword", $pGROUP1 + ($cbSIDATTR * $i)) $sSID = _Security__SidToStringSid(DllStructGetData($tGROUP, 1)) If StringInStr($sSID, "S-1-5-32-544") Then ; member of Administrators group $inAdminGrp = True ; check for deny attribute If (BitAND(DllStructGetData($tGROUP, 2), 0x10) = 0x10) Then $denyAdmin = True ElseIf StringInStr($sSID, "S-1-16-12288") Then $elevatedAdmin = True EndIf Next ; If $inAdminGrp Then ; check elevated If $elevatedAdmin Then ; check deny status If $denyAdmin Then ; protected Admin CANNOT elevate Return SetExtended(0, 0) Else ; elevated Admin Return SetExtended(1, 1) EndIf Else ; protected Admin Return SetExtended(1, 0) EndIf Else ; not an Admin Return SetExtended(0, 0) EndIf EndIf EndFunc ;==>_IsUACAdmin Func _IsUACEnabled() Return (RegRead("HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System", "EnableLUA") = 1) EndFunc ;==>_IsUACEnabled Example #include <_IsUACAdmin.au3> #include <GuiButton.au3> #include <GuiConstantsEx.au3> $g = GUICreate("UAC Test", 200, 100) $b = GUICtrlCreateButton("Elevate", 200-72, 100-27, 70, 25) _GUICtrlButton_SetShield($b) $admin = _IsUACAdmin() $canelevate = @extended GUICtrlCreateLabel("IsAdmin (built-in): " & (IsAdmin() = 1), 4, 4) GUICtrlCreateLabel("_IsUACAdmin (full admin): " & ($admin = 1), 4, 24) GUICtrlCreateLabel("Process can elevate: " & ($canelevate = 1), 4, 44) If $admin Or (Not $canelevate) Then GUICtrlSetState($b, $GUI_DISABLE) GUISetState() While 1 Switch GUIGetMsg() Case -3 ExitLoop Case $b ; restart elevated If @Compiled Then ShellExecute(@ScriptFullPath, "", @WorkingDir, "runas") Else ShellExecute(@AutoItExe, '/AutoIt3ExecuteScript "' & @ScriptFullPath & '"', @WorkingDir, "runas") EndIf Exit EndSwitch WEnd
-
A specific executable compiled with Aut2Exe 3.3.8.1 running under Windows 7.1/64 requests UAC/UAE elevation if it is compiled with the RequireAdmin option. Which is the expected behaviour. However, when the same code is compiled with 3.3.12.0 no UAC prompt occurs, and instead the exe (or possibly the calling program) reports 'CreateProcess failed; code 740' and fails to launch. Just wondering if there are any known differences here. If the issue hasn't been seen before I'll do a few more tests to try and establish under what conditions it occurs.
- 4 replies
-
- UAC
- RequireAdmin
-
(and 1 more)
Tagged with:
-
So im trying to install office 2013 via the OEM click to run app which i get through with "send()" but i need to disable UAC and reboot because of the prompt. you can do this by changing some registry keys but i cant for the life of me get this to run. when i run the following from cmd: ;Run('C:\Windows\System32\cmd.exe /k %windir%System32reg.exe ADD "HKLMSoftwareMicrosoftWindows NTCurrentVersionWinlogon" /v DefaultPassword /t REG_SZ /d password /f ') it tells me the operation completed sucsessfully and the values have changed. when i run the same command from autoit it tells me it was sucsessful however the registry values have not changed. ive tried running as administrator and as a regular user but no dice. ive tried regwrite and also using @comspec. these are the only 4 values i need to change, can someone shed some light on where im going wrong? ;Run('C:\Windows\System32\cmd.exe /k %windir%\System32\reg.exe ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v AutoAdminLogon /t REG_SZ /d 1 /f ') RegWrite("HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon", "AutoAdminLogon", "REG_SZ", "1") sleep(1000) ;Run('C:\Windows\System32\cmd.exe /k %windir%\System32\reg.exe ADD "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v DefaultUserName /t REG_SZ /d Admin /f ') RegWrite("HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon", "DefaultUserName", "REG_SZ", "Admin") sleep(1000) ;Run('C:\Windows\System32\cmd.exe /k %windir%\System32\reg.exe ADD "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v DefaultPassword /t REG_SZ /d password /f ') RegWrite("HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon", "DefaultPassword", "REG_SZ", "password") sleep(1000) ;Run('C:\Windows\System32\cmd.exe /k %windir%\System32\reg.exe ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v EnableLUA /t REG_DWORD /d 0 /f ') RegWrite("HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System", "EnableLUA", "REG_DWORD", "0") sleep(4000) Shutdown(6)
- 2 replies
-
- UAC
- disable UAC
-
(and 2 more)
Tagged with:
-
I have a new Windows 8 computer and it won't compile scripts in my non admin account but it will in the admin account which is fine except that I want to use the non admin account. I have a simple script MsgBox(0,"Test","This is running") and this is the output I get when I try to compile it. >"C:\Program Files (x86)\AutoIt3\SciTE\AutoIt3Wrapper\AutoIt3Wrapper.exe" /ShowGui /in "C:UsersGraeme_2DocumentsTestNon.au3" +>10:58:14 Starting AutoIt3Wrapper v.2.2.0.3 SciTE v.3.4.1.0 Keyboard:00000809 OS:WIN_81/ CPU:X64 OS:X64 Environment(Language:0809) +> SciTEDir => C:Program Files (x86)AutoIt3SciTE UserDir => C:Program Files (x86)AutoIt3SciTEAutoIt3Wrapper -> No changes made.. >Running AU3Check (1.54.22.0) from:C:Program Files (x86)AutoIt3 input:C:UsersGraeme_2DocumentsTestNon.au3 +>10:58:21 AU3Check ended.rc:0 >Running:(3.3.8.1):C:\Program Files (x86)\AutoIt3\Aut2Exe\aut2exe.exe /in "C:UsersGraeme_2DocumentsTestNon.au3" /out "C:UsersGraeme_2AppDataLocalAutoIt v3Aut2exe~AU3yjbyxti.exe" /nopack /comp 2 !>10:58:21 Aut2exe.exe ended errors because the target exe wasn't created, abandon build. (C:UsersGraeme_2AppDataLocalAutoIt v3Aut2exe~AU3yjbyxti.exe)rc:9999 +>10:58:21 AutoIt3Wrapper Finished. >Exit code: 0 Time: 7.94 Any ideas about how I can compile programs in this account welcome. Blessings
-
_RunWithReducedPrivileges An odd thing about Vista+ O/S's is that, once you run a process in elevated privileges mode, you can't run other processes in lower-privileged modes. Why, you ask, would that be important? Sometimes you want - or need - to limit the privileges of a process: A very common scenario for me is drag-and-drop. Windows' Explorer does NOT allow this to occur between lower privileged processes (like Explorer itself!) and other processes. This is very frustrating for users in programs that take advantage of that. There's also some problems using certain SendMessage commands from other unelevated processes.Setting the state or properties of windows that have an elevated privilege may not work either from other unelevated processes..An install or setup program that needs to launch the installed program will more often than not want to run that program on a lower privilege level (for some of the reasons mentioned above)So, after some looking around I found a way of running processes under a lower privilege mode.Check Elmue's comment 'Here the cleaned and bugfixed code' on this CodeProject page to see where my code was ported from:'Creating a process with Medium Integration Level from the process with High Integration Level in Vista' The usage is straightforward for this one: use it like Run/RunWait, but with the command-line as the 2nd parameter. [i.e. _RunWithReducedPrivileges(@ComSpec,' /k title Non-Admin prompt') ] Anyway, hope this helps someone out! Ascend4nt's AutoIT Code License agreement: While I provide this source code freely, if you do use the code in your projects, all I ask is that: If you provide source, keep the header as I have put it, OR, if you expand it, then at least acknowledge me as the original author, and any other authors I creditIf the program is released, acknowledge me in your credits (it doesn't have to state which functions came from me, though again if the source is provided - see #1)The source on it's own (as opposed to part of a project) can not be posted unless a link to the page(s) where the code were retrieved from is provided and a message stating that the latest updates will be available on the page(s) linked to.Pieces of the code can however be discussed on the threads where Ascend4nt has posted the code without worrying about further linking.Download the ZIP from my site
- 1 reply
-
- Reduce
- Execution Level
-
(and 5 more)
Tagged with:
-
I have been using AutoIT for several years now, although mostly with Windows XP. As my company is undertaking a massive Windows 7 conversion, I find that some of the features of AutoIT do not seem to work as I would think they should, which brings about my question today... I use the AutoIt3Wrapper with my compiled scripts and everything works well generally; however, I have a need to include two commands in an AutoIT script that have to be RunAsAdmin. I have the AutoITWrapper set as "#AutoIt3Wrapper_Res_requestedExecutionLevel=requireAdministrator" and I am prompted for UAC elevation. The commands; however, do not seem to be elevating. RunWait(@ComSpec & ' /c bcdedit /set {default} recoveryenabled No', @HomeDrive, @SW_HIDE) RunWait(@ComSpec & ' /c bcdedit /set {default} bootstatuspolicy ignoreallfailures', @HomeDrive, @SW_HIDE) If I post the commands into an elevated command prompt they work correctly, but via the script they seem to be ignored. I appreciate any ideas and/or assistance. Thanks In Advance!!!
- 3 replies
-
- #RequireAdmin
- UAC
-
(and 1 more)
Tagged with:
-
Hi I hope someone can clarify an issue that I am having with regread reporting under W7 were I have administrative rights on the machine The situation is that I am performing the following code in a for loop against an ini file under but I am getting contradictory results depending on whether I engage UAC for the script $Transaction = RegWrite($vidBranchPath & "\" & $iniFileSectionUSB[$i][1]) $Transaction = RegRead($vidBranchPath & "\" & $iniFileSectionUSB[$i][1], "") If I run the script without UAC the script does not error branch even though the previous regwrite has not successfully completed the write task. If I engage UAC the registry entries are created. My concern is not that the entries are not being created but that under non-UAC the regread is reporting their existence.
-
I could not find a User account script on these forums that was satisfactory, a On/Off setting is quite useless if it cant be configured, so i wrote this up. Should work on both x64 and x86 compiled scripts. Windows7 and Vista. Functions: Example: Script:
-
I previously ran SciTE and Autoit from a Windows XP machine and therefore didn't have any UAC or privileges issues to deal with. Now I'm running Win7 64 bit and noticed that when opening a .au3 file I don't get any prompt choice to run as admin. It simply opens the file I requested. When I hit F5 or click on "Go" to run the application SciTE is unable to hook into the app and get Console output when run like this. I can, however, go through the trouble of opening SciTE independently as administrator before opening the source code .au3 files and when I hit f5 or "Go" like this I am again able to get ConsoleWrite output as well as get runtime errors. My question: Is it possible to modify the SciTE editor so that it prompts to run as administrator when attempting to open a .au3 file rather than right clicking on SciTE and manually selecting to run as administrator and then opening the .au3 file? I'm trying to achieve a shortcut and save time while removing one more annoyance that is UAC Win7 powered. Many thanks!
-
This is a question for Systems Administrators of all kinds - those who manage software on a domain where users have restricted rights - and who have Windows 7 computers in their domain. How do you get around UAC to install Software or Certificates remotely and without user intervention? ... and without being logged in to the computer. ( There is no such thing as "right click and.." answers. We have over 3000 computers! ) I've tried scheduled tasks (schtasks.exe) with the /RL HIGHEST switch - no good. I've even looked into PowerShell 2.0 - but it is not what I need. Even with UAC disabled, some things still need the "Run As Administrator" privileges to actually install properly. Has Microsoft completely screwed Systems Administrators with this UAC ??
-
_ShellExecuteWithReducedPrivileges An odd thing about Vista+ O/S's is that, once you run a process in elevated privileges mode, you can't run other processes in lower-privileged modes. Why, you ask, would that be important? Sometimes you want - or need - to limit the privileges of a process: A very common scenario for me is drag-and-drop. Windows' Explorer does NOT allow this to occur between lower privileged processes (like Explorer itself!) and other processes. This is very frustrating for users in programs that take advantage of that. There's also some problems using certain SendMessage commands from other unelevated processes.Setting the state or properties of windows that have an elevated privilege may not work either from other unelevated processes.An install or setup program that needs to launch the installed program will more often than not want to run that program on a lower privilege level (for some of the reasons mentioned above)So, after some looking around I found two ways of running processes under a lower privilege mode. One is using CreateProcessWithTokenW (see ), and the other is using COM objects - specifically Windows Explorer's SHELL object to ShellExecute a command/program. This can be used just like AutoIt's built-in ShellExecute() function, but of course the program that runs will be at a reduced IL (integrity level). The code is based on Brandon @ BrandonLive's article here: 'Getting the shell to run an application for you - Part 2:How | BrandonLive' The usage is straightforward for this one: use it like ShellExecute. The $bWait parameter is only there in case ShellExecuteWait() will be called for either non-elevated processes or pre-Vista O/S's. Example: _ShellExecuteWithReducedPrivileges(@ComSpec,' /k title Non-Elevated prompt (via Shell.ShellExecute)') Anyway, hope this helps someone out! Ascend4nt's AutoIT Code License agreement: While I provide this source code freely, if you do use the code in your projects, all I ask is that: If you provide source, keep the header as I have put it, OR, if you expand it, then at least acknowledge me as the original author, and any other authors I creditIf the program is released, acknowledge me in your credits (it doesn't have to state which functions came from me, though again if the source is provided - see #1)The source on it's own (as opposed to part of a project) can not be posted unless a link to the page(s) where the code were retrieved from is provided and a message stating that the latest updates will be available on the page(s) linked to.Pieces of the code can however be discussed on the threads where Ascend4nt has posted the code without worrying about further linking.Download the ZIP from my Site
-
- Reduce
- Execution Level
-
(and 7 more)
Tagged with: